Security best practices for web and mobile app development
In a recent article, Infosecurity predicts an increase in the following application security threats in 2022:
- Ransomware and cyberterrorism
- Cryptocurrency thefts
- Vulnerabilities in supply chain security systems
- Zero-day vulnerabilities
- Deepfake attacks
These are cybersecurity attacks that require attentiveness and decisive action to protect against.
According to Forbes, in 2022, application security protection methods will be dominated by role-based access control (RBAC) mechanisms, multi-factor authentication (MFA), virtual private networks (VPNs), and automated data backup and data recovery mechanisms.
A careless attitude to the above-mentioned threats and security protection methods may lead to severe vulnerabilities in an application’s security system.
Learn from the Yalantis experience how to ensure top-tier security for your software system
DOWNLOAD SECURITY RECOMMENDATIONSConsequences of neglecting cybersecurity measures explained with real-life examples
In 2021, these stories conquered the headlines of news outlets around the world, highlighting once again the importance of using proper cybersecurity measures to protect systems from severe attacks:
- In March 2020, SolarWinds delivered an update to the Orion system to their 33,000 customers that contained a malicious piece of code. This malicious code worked as a backdoor for hackers and resulted in a data breach. BitSight estimated $90 million in losses as a consequence of this cyberattack.
- In May 2021, Colonial Pipeline faced a cybersecurity attack, due to which the Department of Transportation declared a regional state of emergency. Hackers penetrated the system using compromised employee credentials and demanded a $4.4 million ransom from the company. The hack caused the first ever shutdown of the Colonial Pipeline gas pipeline system according to Joseph A. Blount, Jr., the company’s CEO and president. In the end, Colonial Pipeline paid nearly $5 million in cryptocurrency to get a decryption key from hackers and unlock their data network.
Nobody knows when an attack on your system may occur, what consequences your company will face, and what losses to expect. In today’s article, we describe how Yalantis protects applications at each stage of development and where an application’s security should really start.
Where does application security start?
Application security starts long before a software development company concludes a contract to build a product. At the outset, the development company has to accommodate and document specific security routines and principles and set them out in its information security policy.
An information security policy, or ISP, isn’t just a set of rules; it’s a mindset a company adopts to ensure proper security precautions with respect to the software they create.
Why is an information security policy important for software development companies?
A security policy is a guide to proper application development and protection. Technical specialists use security policies to correctly maintain an application’s security, quickly and properly respond to urgent incidents, and ensure compliance with cybersecurity standards. This guarantees to the client that the development company applies security best practices and regularly updates and enriches its knowledge base.
Every company’s security policy may differ significantly. New employees can apply methods learned from previous experiences that may contradict their new company’s security requirements. That’s why Yalantis follows the latest trends in information security and considers personnel training as an essential component of our company’s security.
What falls within an information security policy and who is responsible for managing it?
A company’s information security policy includes requirements for the development process and employees’ security activities:
- Security requirements for solution development present guidance on ensuring an application’s compliance with modern security standards. Simply put, a security policy incorporates a company’s views on cybersecurity and includes management of roles and responsibilities, data breach policies, disaster recovery and business continuity plans, secure coding practices, as well as application security monitoring practices and standards.
- A company’s internal requirements cover employees’ work behavior and actions. They may include protections for personal devices, NDA requirements, remote access policies, and more, along with disciplinary actions for violating the requirements.
Creating and updating security policies is a cooperative process. A Chief Information Security Officer, or CISO, is an officer-in-charge who takes responsibility for implementing and overseeing compliance with security requirements.
Other specialists, such as directors of engineering, web development, and architecture design constantly contribute to implementing new practices, following new standards, and training staff.
A security policy is the first step in secure app development. As soon as requirements are set and the company’s specialists acknowledge their dos and don’ts in terms of architecture design, coding practices, and so on, the actual development starts.
Ensuring application security via a secure development lifecycle
The secure development lifecycle, or S-SDLC, represents particular security practices at each stage of application development. Adhering to the S-SDLC helps our specialists build high-quality and secure development processes. Such an approach helps to predict vulnerabilities that may occur at all stages of development and protect the application from them.
Advantages of S-SDLC adoption include:
- A carefully crafted architecture that complies with security standards, laws, and regulations that a business should comply with
- Lower expenditures due to meticulous investigation of potential vulnerabilities and their prevention through applying specific coding practices and security attributes
- An impenetrable application thanks to previously assessed security risks and a properly built protection system
- A rich knowledge base of high-class security measures. Information security specialists constantly update their knowledge of security vulnerabilities and means of averting and dealing with them.
- Higher customer satisfaction, as during negotiations and concept approval, a development company will be able to present customers with proven methods for data protection.
In general, an S-SDLC is similar to a software development lifecycle (SDLC) but with a substantial focus on security:

Learn more about how we establish a secure SDLC in our client’s project.
Let’s look at each stage in detail to reveal cybersecurity practices that Yalantis adheres to.
Development planning: coming up with a security strategy
The planning stage helps security specialists to design a security strategy for the project. Yalantis specialists consider location-, industry-, and product-specific requirements and tailor the development process to them. Sometimes, we conduct workshops for customers and development team members to make sure everybody acknowledges the specifics and risks of working with specific security requirements and their violation.
At the planning stage, the goal is to build a plan of action to protect the system from vulnerabilities. This plan includes technological security instructions. Considering them in advance, we help our customers obtain certifications required for operating in a specific niche or a specific territory.
For example, to distribute healthcare software in the USA, a customer’s application has to meet HIPAA (Health Insurance Portability and Accountability Act) security requirements. The most suitable security frameworks for this are NIST, HITRUST, CSO, ISO, and COBIT. If our customer’s goal is compliance with the GDPR, we will refer to the local frameworks, e.g., BS 10012:2017 (British Standard) and ISO 27701 security frameworks. There are also situations when developers create a solution relying on several frameworks simultaneously.
Yalantis has experience ensuring an application’s compliance with HIPAA requirements and obtaining ONC Health IT Certification. Going beyond the healthcare borders, we’ve also helped our clients obtain PCI DSS (Payment Card Industry Data Security Standard) certification for FinTech solutions.
After the planning stage is over, it’s time to start creating the solution architecture.
Application architecture design: what to consider ahead
The solution architecture is not just the scheme of the solution’s components and their interoperability. Documentation, risk mitigation strategies, and disaster recovery plans are laid out at the very beginning because they give directions to the development and quality assurance teams.
At the architecture stage, we decide on security components and evaluate how the team will construct them at further stages of secure web and mobile application development. Our specialists usually consider the CIA triad, which stands for confidentiality, integrity, and availability.
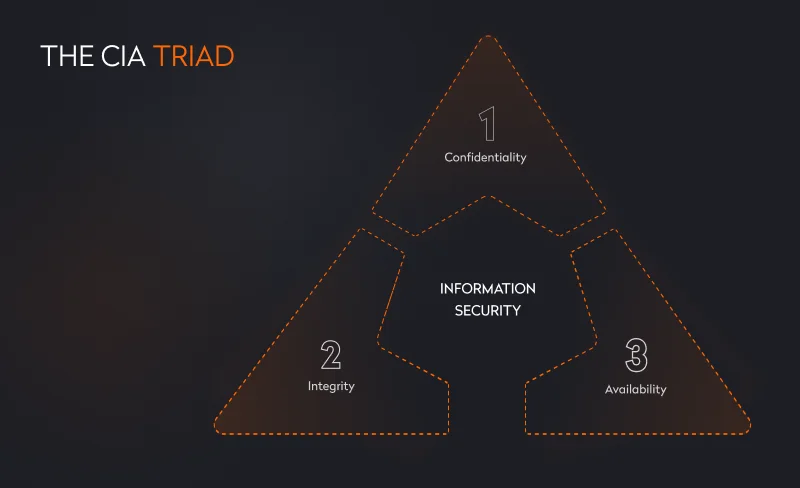
Let’s describe the triad in detail.
1. Confidentiality
Confidentiality is about keeping an application’s data private and making sure the system gives access to the right users. For instance, to make sure that user data won’t be handed to the wrong person, solution architects and app developers have to take care of access controls and build a reliable IAA (identification, authentication, and authorization) scheme.

Identification is the process of identifying a user in the system, usually by a username or email. When registering, a user provides this identifier and a password to create a unique user account in the system to which their data will be linked. Then users authenticate in the application with these identifiers and passwords.
Specialists can choose among five types of authentication:
- Password-based authentication is one of the most common types: a user accesses an application after entering a username and password. Despite being widely used, this option is pretty weak against phishing attacks because people can use one weak password for multiple services.
- Certificate-based authentication uses cryptography and works through digital public key certificates. These certificates allow users to identify themselves before getting access to an application. Certificate-based authentication is stronger than password-based authentication.
- Biometric-based authentication considers a user’s biological characteristics such as face, fingerprint, voice, or iris. It’s often used in multi-factor authentication thanks to its high security guarantees.
- Token-based authentication is a popular method for authenticating users through a unique combination of letters and/or numbers users get after entering their credentials. This type of authentication is considered highly secure due to the use of personal devices such as smartphones that are always by a user’s side. If users get an unsolicited verification code, they can recognize an attempt of unauthorized access. Still, there’s always the risk that an attacker can steal a token.
- Multi-factor authentication implies the use of several types of authentication. For instance, users can enter a password, enter a received verification code, and then use a form of biometric authentication to get access to an application.
The choice of authentication type depends on the product. If it’s an in-house platform for internal management, password-based authentication is enough. However, don’t forget the Colonial Pipeline case. If the application is for a wide audience, you have to consider stricter measures, such as multi-factor authentication. This is especially crucial for healthcare and banking applications.
Authentication is followed by authorization, which gives users access to the system. To ensure secure user authorization, we have to decide on a method of authorization that prevents data leaks. The most commonly used methods are API keys, Basic Auth, HMAC, and OAuth 2.0.
During authorization, the system also recognizes a user’s access rights to resources. For this, roles should be assigned to each user. For example, a user can 1) only read data, 2) read and edit data, or 3) read, edit, and delete data. Role-based access control (RBAC) not only protects data but prevents unauthorized users from modifying or deleting it and protects data from problems caused by human factors.
2. Integrity
Integrity guarantees that a user’s data is in its original state. In order to keep data unchanged, various security mechanisms are used, such as:
- data encryption
- digital signatures
- systems for detecting database attacks
- previously mentioned authentication and authorization mechanisms
It’s also necessary to focus on non-repudiation. Non-repudiation is about recording actions of authorized users to confirm their authorship.
3. Availability
Availability guarantees that the application is available to users, the application works properly, necessary data is loaded, and the application performs smoothly. In order to ensure constant availability, experts develop mechanisms to protect databases from external influences. This concerns the development of disaster recovery plans and strategies for assessing possible risks. In the event of system problems, information security specialists carry out a detailed analysis and update recovery plans.
Once solution architects and developers have chosen methods for protecting the application, they can proceed with working on the secure application development.
Application development: taking proper security measures
At the beginning, the team lead chooses a tech stack, taking into account product, industry, and location requirements for storing and gathering data. This decision is important because choosing the wrong tech stack that doesn’t comply with requirements can throw the development team back to the beginning of development. In other cases, developers might change the development path right in the middle of the process because already written code wouldn’t meet security requirements.
Unprotected code can become a weak point in the system and lead to data breaches, code injections, and so on. To avoid such problems, it’s necessary to consider best practices for safe coding. The most popular are those from the OWASP Secure Coding Practices Checklist. Our specialists always adhere to these practices when writing code in order to protect the system from outside interference and prevent errors. OWASP practices include:
- input validation
- output encoding
- authentication and password management
- session management
- access control
- cryptographic practices
- other aspects outlined in the official OWASP guide
Yalantis holds special training for new staff, demonstrating right and wrong approaches to coding with real examples.
It’s also common practice to regularly check code as it’s written. Such checks are best performed using special tools for static code analysis and with the involvement of other specialists on the team than the author of a piece of code. This helps developers find and eliminate vulnerabilities even before the application is deployed and significantly reduces the risk of vulnerabilities appearing at the production stage.
SAST tools for code review
Static application security testing (SAST) tools scan code for flaws that can lead to serious security vulnerabilities. These tools are used in the early stages of application development since SAST tools don’t require a ready-made application to scan its code. SAST tools validate code in real time and report problems to developers immediately.
The benefits of SAST tools are in their speed and volume. They can check a huge number of lines of code in minutes and provide a report on vulnerabilities found. A human check would take a significant amount of time, and it’s not a given that people would be able to detect all problems themselves.
At Yalantis, we strongly recommend that our customers automate code verification with SAST tools. With automated code verification, developers regularly receive scan results of their code and can gradually fix all errors.
After code is validated by team members,SAST tools, and other code analysis tools, the application moves to the deployment stage.
Application deployment: building strong infrastructure protection
Application infrastructure combines a number of components, among which application networks play a considerable role. Most often, application components transmit information through APIs that can be compromised. Therefore, the system needs strict protection. Let’s take a look at the most common infrastructure security threats and how Yalantis protects it during deployment.
The most common software security threats
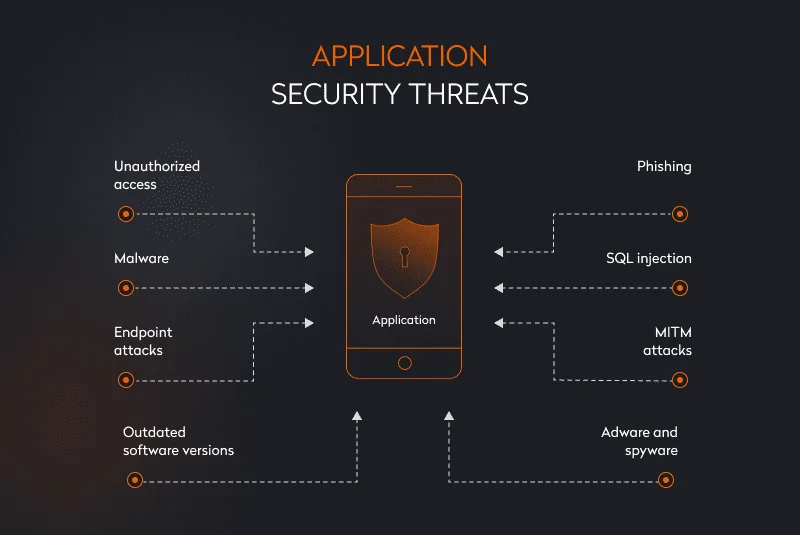
- Unauthorized access is the most widespread reason for data breaches. In this type of attack, unauthorized users penetrate the system and steal users’ personal data and the history of activities inside the application.
- Malware (short for “malicious software”) can be in the form of a file or a piece of code that infects the system and gathers an end user’s private information.
- Endpoint attacks are attacks on users’ devices, such as smartphones, computers, laptops, and tablets. This list can also include servers and network-attached storage. Such attacks can result in data theft and system disruption.
- Outdated software versions can contain vulnerabilities and flaws in cybersecurity measures. Hackers use these loopholes to steal personal data.
- Phishing is well-known, and users seem to be aware of how dangerous links from unknown sources are; however, there’s still a high chance of facing phishing attacks from entities disguised as trusted sources.
- Adware and spyware work in a similar way. Whereas adware comes to a user through advertising pop-ups on websites and can lead to infected web pages, an infected page can start downloading infected software (spyware) to a device on its own. This software can penetrate the system to gather user data.
- MITM attacks, or man-in-the-middle attacks, count on interfering in the communication of two or more parties to steal credentials or any other type of personal data.
- SQL injection aims at getting into the backend database to steal hidden data from end users.
To avoid these dangers during deployment, specialists should follow company-specific security practices.
Yalantis infrastructure protection best practices
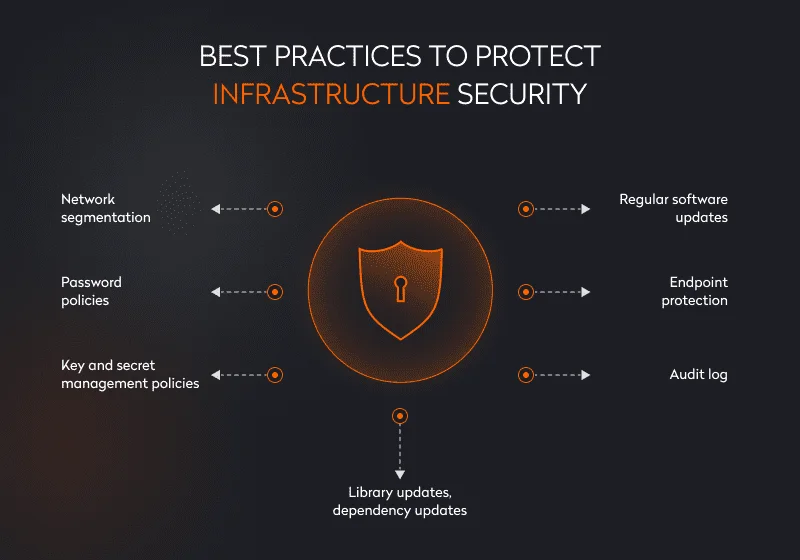
- Network segmentation. By segmenting the network into multiple physical and logical subnets, administrators can more efficiently control traffic between those subnets according to security parameters. This approach helps to save the system from data breaches, infections, and similar cybersecurity threats.
- Password policies cover external and internal user password management. External measures include assessing the complexity of user passwords when users sign up in the system and offering to create stronger ones. Internal password policies concern methods of storing passwords in databases, such as password encryption.
- Key and secret management policies. These policies include rules on the creation, storage, exchange, and updating of keys and user credentials in the system. They are securely kept in special key management services that encrypt data by default, such as AWS KMS, Google Cloud KMS, or Azure Key Vault. Without these services, developers would keep all keys and secrets in code or configuration files, which are easier to attack.
- Library updates. Frameworks and programming languages are constantly updated. Usually, these updates bring innovations to cybersecurity measures, helping to protect the application.
- Dependency updates. Dependencies include external libraries you use in the application, such as encryption mechanisms. You should always keep track of dependency updates and implement new versions of dependencies right after they’re released.
- Regular software updates. At Yalantis, it’s crucial for specialists to constantly monitor a system’s cybersecurity well-being and update the software to protect clients and their customers from data breaches.
- Endpoint protection. The protection of endpoints, such as servers and user devices, occurs through endpoint protection platforms (EPP), which act like antivirus software, protecting a device from security threats and malware, filtering traffic, and blocking a user’s USB device if needed.
- An audit log is a record of user actions. It records who performed an activity, when the activity was performed, and how the system responded to these actions. It’s important to emphasize that logs don’t contain any details about transmitted data.
Implementing proven and reliable security practices is great. However, you still have to check how the application works after specialists apply these practices. For this, development companies perform penetration testing to discover hidden or unnoticed security vulnerabilities.
Penetrate your application to test its security
Penetration tests analyze an application’s security by carrying out attacks on the application or its infrastructure.
This practice helps to protect the system from real hackers by removing loopholes they could take advantage of. Pentesters use special techniques to test applications qualitatively.
Penetration testing techniques
- Black box testing is conducted from the user’s perspective to check functional and non-functional aspects of an application’s work. This type of testing is done through direct interaction with the interface. Testers don’t know how the system works from the inside and look for issues and vulnerabilities by manually checking all buttons, forms, transitions, etc.
- White box testing is testing with knowledge of the application’s internal structure. Testers take into account the application’s code, architecture, and configurations. Based on this, they analyze the expected response to each command and the actual result. In this way, the correct work of the application and data output are assessed.
- Gray box testing is a combination of black box and white box techniques. In gray box testing, testers have a minimal amount of information about the inner workings of the application and evaluate it from the user’s perspective. Thus, they can effectively check the application’s functionality.
During penetration tests, testers check the system for the most common threats outlined in the OWASP Top 10. This is a document that OWASP publishes every year, evaluating the most common application security risks. These were the top risks in 2021:
- Broken access control
- Cryptographic failure
- Injection
- Insecure design
- Security misconfiguration
- Vulnerable and outdated components
- Identification and authentication failures
- Software and data integrity failures
- Security logging and monitoring failures
- Server-side request forgery
It’s important to mention that these risks aren’t the only ones to test applications for. These are just the most widespread. Our specialists take into consideration the industry an application will operate in, then extend the list of vulnerabilities to check the application for.
Penetration testing consists of several steps that also include preparing for testing and evaluating testing results.
Penetration testing stages
Penetration testing comprises four stages:
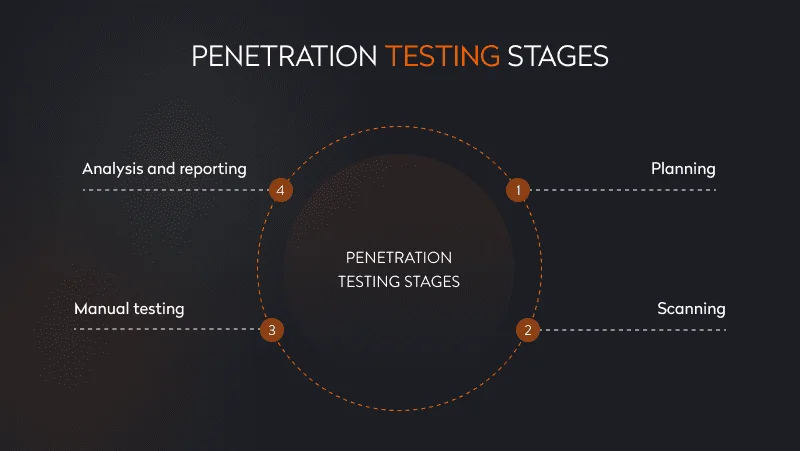
- Planning: The team sets testing goals, selects the components of the application to be tested, and decides on testing techniques. Based on the components, pentesters draw up a list of security threats to test for.
- Scanning: Pentesters conduct static and dynamic tests, during which they check the system’s response in real time to evaluate the application’s performance.
- Manual testing: Pentesters try to gain access to the application by simulating an attacker’s activities.
- Analysis and reporting: The final stage involves analysis of identified vulnerabilities and drawing up a report on them with recommendations for developers.
To assess cybersecurity risks, pentester engineers use special methodologies that describe each step of a risk assessment with detailed instructions.
When the application is ready for production, it’s necessary to conduct benchmark testing, simulating an external hack of the system.
After the application is tested and optimized by the development team, it can go to the production stage. However, there is one last thing to do: ensure the system is protected from distributed denial-of-service (DDoS) attacks and harmful traffic. For this, we use a web application firewall.
WAF to protect the application after its release
A web application firewall, or WAF, monitors and filters malicious traffic and protects the application from DDoS attacks, bot traffic, cross-site forgery, cross-site-scripting (XSS), file inclusion, SQL injection, and other types of attacks.
WAFs can be of three types:
- Network-based that protect hardware
- Host-based that are implemented in the application software
- Cloud-based that protect cloud-based applications
A WAF works as an intermediate layer between the application and the internet and follows security policy standards that allows it to identify traffic that is considered malicious. Thus, it protects the application and prevents unauthorized data breaches.
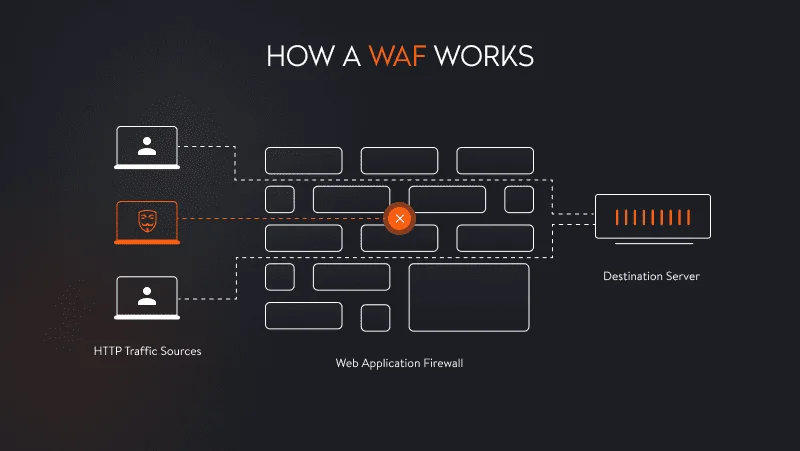
A WAF requires investments, but this technology pays for itself. For companies that work with sensitive user data, a WAF is a must. Cheap and weak WAFs don’t filter traffic properly and may make your application vulnerable.
You may also be interested in our expert article on SaaS cloud migration.
In closing
Application security doesn’t end at this point. It also consists of multiple post-release activities that specialists should take care of during the whole period of an application’s existence. Times change, and so do security practices and requirements. Yalantis often provides post-release security support to applications to make sure the system runs like clockwork and doesn’t have any weak spots. In long-term partnerships, we also provide security audits and implement new security measures when new guidelines come out.
Rate this article
5/5.0
based on 3,198 reviews