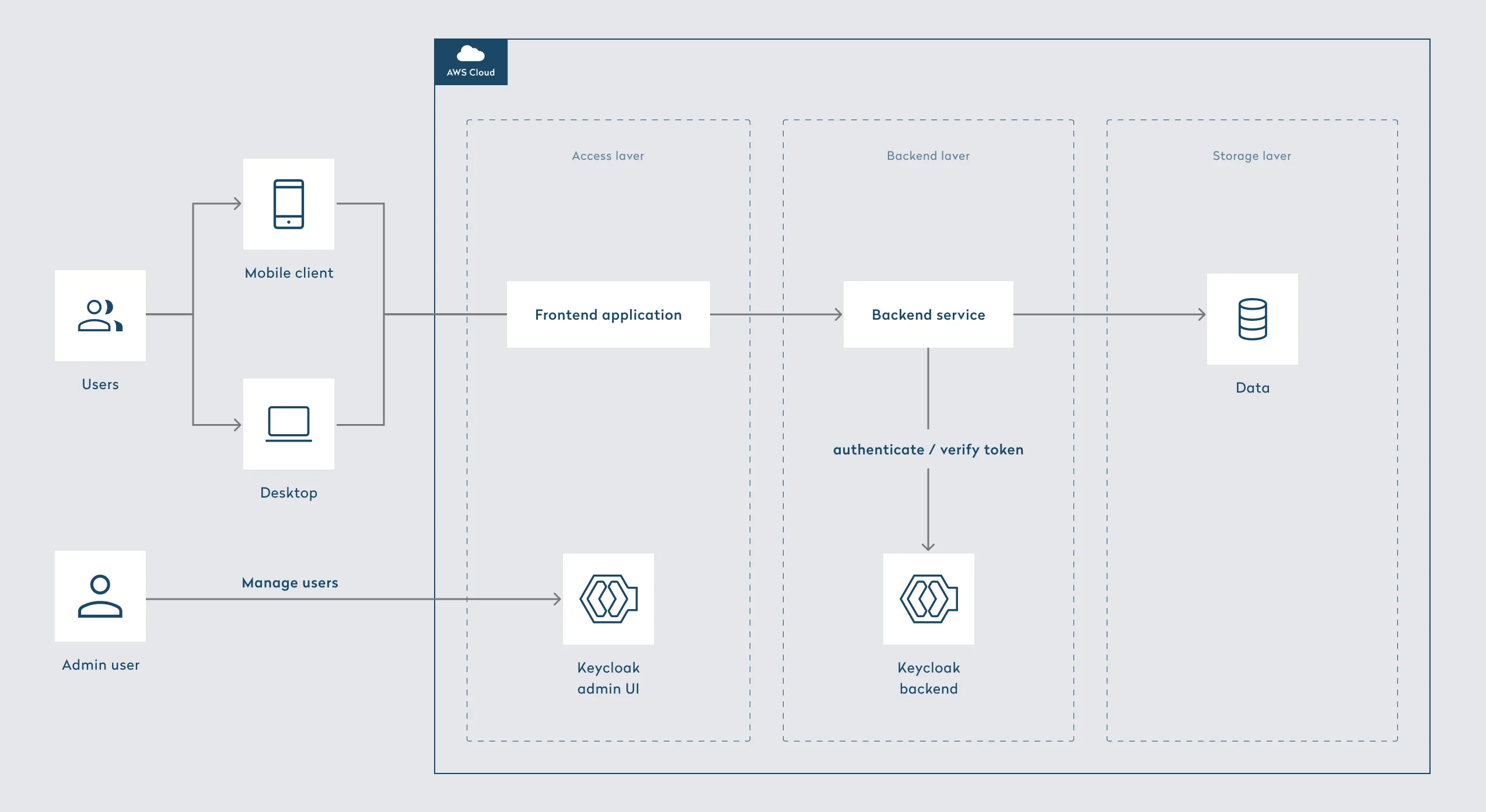
Platform overview
Authorization Accelerator is one of the Yalantis Platform Core solutions, allowing expedited deployment of a ready-to-use secure module for user authorization across multiple domains. It’s supplemented with industry-required functionality for secure authorization, such as:
- strong authentication
- fine-grained authorization (FGA)
- role-based access control (RBAC)
- brute-force protection
- advanced user management
- extendable functionality for user federation
- secure sessions
- and more
Yalantis Authorization Accelerator facilitates development processes for the entire project team and saves valuable resources.
Common challenges businesses face when implementing authorization
Implementing authorization functionality is one of the primary steps in developing a software solution, regardless of the industry. Despite being relatively simple to develop, an authorization module serves as the first layer of security in the user journey and is critical to any solution’s ability to function. That’s why security measures incorporated in any authorization solution must be constantly updated, leading to additional time and resource investments.
All of these factors force businesses to balance between delivering a robust authorization module and saving money for further development. This may culminate in:
- Delayed time to market and a late start in developing business-critical functionality. When developing authorization functionality from scratch, development teams spend lots of time and money on establishing business processes, infrastructure, efficient automation with CI/CD pipelines, etc. This results in failure to meet the production schedule and loss of market share.
- Resource-intensive development. Development from scratch with all operations and features planned, designed, and built from the ground up leads to wasting time on basic operations that companies can easily finish three times faster by integrating ready-to-use products.
- Mediocre user experience. A poor UX frequently results from an in-house team’s lack of expertise in delivering intuitive products. Such a lack of expertise may lead to a low client retention rate, poor system performance, and an inability to handle high loads.
- Poor security due to incomplete implementation of security requirements. Insecure development stems from in-house teams working solely on one product and lacking the required knowledge for building products that meet compliance requirements. As a result, products developed by in-house teams struggle with multiple vulnerabilities related to secure data storage and management.
- Lack of flexibility. Due to limited time for development, businesses risk joining the market with unstable products that can’t scale, won’t let the company grow, and will constantly require additional resources for bug fixing and redevelopment.
- Poor budget and time allocation. Inefficient resource management deprives businesses of the opportunity to build killer functionality at the MVP stage due to spending significant resources on basic features. The consequence is lack of a competitive advantage and failure to gain investors’ trust.
Keeping these challenges in mind, Yalantis developed the Authorization Accelerator. It eliminates concerns regarding resource allocation, delayed time to market, and an insufficiently reliable security system.
Business benefits of Yalantis Authorization Accelerator
-
01
38% to 45% faster authorization module development. Using Yalantis Authorization Accelerator, businesses can save up to 45% of their development efforts on delivering standard user authorization functionality. This is possible owing to a prebuilt module that only needs to be deployed and tailored to business requirements.
-
02
3X quicker project bootstrapping with fewer resources. The accelerator allows development teams to conduct the first demo session within the first sprint rather than after two months of active development and save substantial funds.
-
03
Risk-free implementation and stable performance under high loads. The accelerator’s implementation and operation have been thoroughly tested with real users on various projects in multiple domains. With each new use case, the Yalantis team modifies the platform to ensure it’s able to withstand any possible implementation risks. The accelerator’s lightweight design, speed, and scalability contribute to its excellent performance.
-
04
Flexibility in customization and technological independence. The accelerator can be used for developing any application regardless of the programming language used. It depends only on your business needs. The Yalantis team can easily customize the solution and tailor the authorization process to meet your unique requirements.
-
05
Minimal security risks and efficient access management. Yalantis Authorization Accelerator is built with security best practices in mind to reduce the risk of common security vulnerabilities, protecting sensitive data from unauthorized access. For access management, we implemented standard protocols such as OpenID Connect, OAuth 2.0, and SAML 2.0, which have proven to be reliable industry standards. Additionally, with a private KeyCloak setup, the solution guarantees strict identity protection.
Use cases of Yalantis Authorization Accelerator
-
Web and mobile application authorization to ensure that only authorized users have access to a solution and can work with confidential data it contains
-
Role-based access control (RBAC) for businesses to configure their own access control policies and restrict access to specific resources and features within applications
-
Authorization compliant with industry security standards, laws, and regulations such as the GDPR, HIPAA, and PCI DSS
-
Reduce development costs while preserving faster time to market due to advanced authorization functionality
Role-based functionality for ensuring secure authorization
Yalantis Authorization Accelerator provides businesses with the following features:
User features based on KeyCloak integration
- Sign up: The accelerator includes all parameters (email, full name, phone number, password, address, profile picture, etc.) required for users to register in the system according to validation rules (configured in KeyCloak).
- Sign in: The accelerator offers several ways for users to log in, which can be configured based on your application’s needs. Methods include single sign-on (SSO), identity brokering, social login, simple login credentials (username and password), multi-factor authorization (MFA), and more.
- Password reset: The accelerator provides a password reset page where users can enter a new password for their account. KeyCloak allows administrators to set password policies or complexity requirements based on their business needs.
- Log out: Users can initiate the logout process by clicking a Logout button or a similar link in the application’s user interface.
Key admin features and capabilities
Yalantis Authorization Accelerator offers features for managing user accounts, roles, and permissions.
- User management: Administrators can create, modify, and delete user accounts; search and view user profiles; enable user self-registration; import users from external sources (such as LDAP); and manage user groups and roles.
- RBAC: Administrators can define and manage roles and permissions, assign roles to users and groups, and implement fine-grained access control policies.
- Password policy: The admin feature set enables administrators to define password policies, including minimum password length and complexity requirements (e.g., requiring special characters); set password expiration and reset rules; and enforce password history and reuse restrictions.
Additional feature set
- Advanced multi-factor authentication (MFA): The accelerator supports various MFA methods, including one-time passwords (OTP), time-based OTP (TOTP), SMS-based authentication, and email-based authentication. Users may need to provide additional factors to log in depending on the configured policies.
- CAPTCHA integration: To prevent automated abuse of the password reset feature, the accelerator supports integration with CAPTCHA mechanisms.
- Session management: Administrators can monitor and manage user sessions, set session timeout and idle timeout policies, and implement SSO and single logout (SLO).
Please note that this product is constantly being updated, and this is not a complete list of functionality. Contact us for more information.