When you think of business sectors that have seen constant growth for the past decade, the healthcare sector probably comes to mind. Statista projects that total health spending per person in the US will increase to $1,515 by 2050. Another authoritative source, Deloitte, indicates that 72% of consumers prioritized their personal health and wellbeing in 2021.
Healthcare concerns became an urgent priority with COVID-19, which accelerated global digitalization and made healthcare providers invest in advanced technologies to keep pace with the competition.
Creating software to meet healthcare needs is a promising but cumbersome endeavor. Following industry requirements, and namely complying with the Health Insurance Portability and Accountability Act (HIPAA), is an unavoidable part of your software development lifecycle in this domain.
What is HIPAA and why is it important?
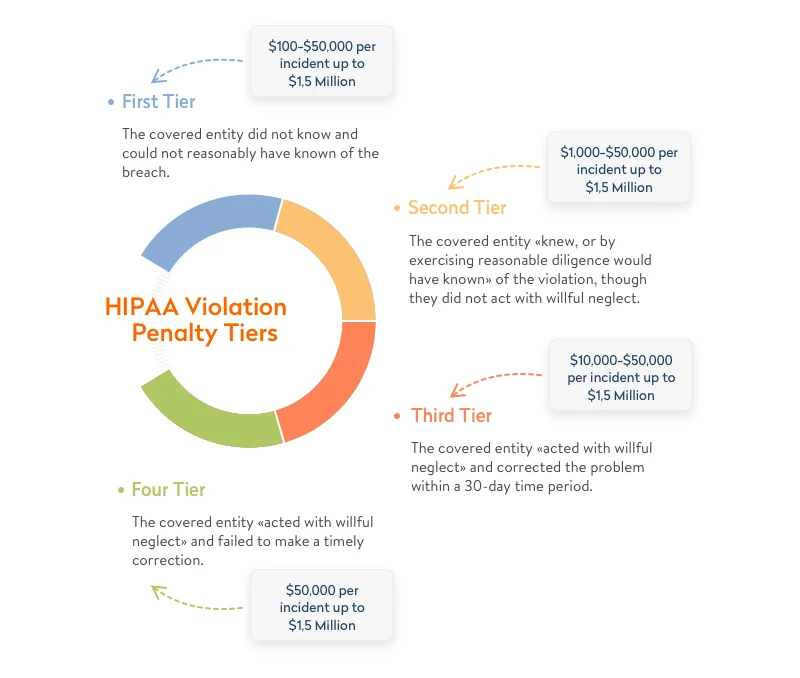
HIPAA is a US law that lays out rules to protect against disclosure of sensitive patient health information. Following these rules for healthcare is a must if you are developing a medical web app system, medical e-prescription system, or some other type of software within the healthcare domain. Fines for violating HIPAA requirements range from $100 to $50,000 per record, depending on the reason for the violation.
According to Compliancy Group, data breaches cost Lifetime Healthcare Companies a total of $5,100,000 in 2021, which was the highest penalty of the year. This is only one of the numerous fines worth millions of dollars issued by the Department of Health and Human Services (HHS) Office for Civil Rights year after year.
Whenever you develop custom healthcare software, build IT systems in medical organizations, develop a hospital management system, or provide any service for healthcare organizations, you need to make sure your product is HIPAA-compliant. Otherwise, you risk losing millions of dollars, your reputation, and even your business.
Learn how we built compliant and connected software for medical devices
Which health applications need to comply with HIPAA rules?
Understanding the applicable rules and taking HIPAA standards into account is a vital part of custom healthcare software development. But what exactly falls under HIPAA’s purview?
The two criteria that define whether an app will be regulated by HIPAA are the type of entity that uses the app and the type of data the app generates, stores, and shares.

Type of entity that uses the app
According to the US Department of Health and Human Services, HIPAA rules apply to covered entities and business associates. These are individuals, organizations, and agencies that produce, access, process, or store protected health information (PHI).
- By covered entities, the Department of Health and Human Services means healthcare plans, healthcare providers, and healthcare clearinghouses that transmit any information in an electronic form. This includes electronic transactions and money transfers. In practice, covered entities are doctors and the hospitals they work for. Therefore, HIPAA compliance is required for software aimed at facilitating doctor-patient interactions, for example, appointment scheduling software. At the same time, if your tech solution involves no covered entity (for example, if it’s a personal women’s health tracker or a prescription reminder app), it doesn’t fall under HIPAA.
- Business associates are humans or organizations that store, collect, process, or transmit protected information on behalf of covered entities. Examples of business associates are attorneys, third-party administrators, accountants, and any digital providers that have access to protected health information (cloud storage providers, email encryption providers, software providers, etc.).

For detailed information about specific entities regulated by HIPAA, you can consult guidance by the US Department of Health and Human Services.
Data covered by the app
In terms of HIPAA, the data we talk about is typically personal health records and any medical information used for patient identification, for instance, medical images. This also includes sensitive data on diagnoses and prescriptions. This information is also referred to as protected health information, or PHI. Keep in mind that healthcare data can be classified as PHI only if medical data and personally identifiable information are combined.
Let’s say there’s an app that helps psychotherapists diagnose mental disorders by studying images with human poses and facial expressions. If the photos are anonymous, there’s no way in which the app can identify patients. But if each photo is associated with a specific patient, such images are considered PHI, and the app falls under HIPAA rules.
In other words, compliance with HIPAA requirements is a must for health applications that contain individually identifiable data that’s stored locally or on a third-party server. If you plan to develop a healthcare software platform like this, make sure it satisfies all requirements from the HIPAA compliance checklist.
Interested in compliant healthcare software development?
We deliver custom software for connected medical devices, clinical process automation, and healthcare apps.
HIPAA audit checklist
Covered entities and business associates are subject to regular HIPAA audits. A HIPAA audit has two critical goals:
- Ensure that all vulnerabilities are mitigated
- Verify that the product meets HIPAA requirements
Audits may differ depending on the type of covered entity or business associate. Below is a checklist of procedures, policies, documents, information, devices, and software that fall under a HIPAA audit:
- Policies that address prevention, correction, detection, and containment of security violations
- Background checks of employees and confidentiality agreements
- Regulations establishing user access for new and existing employees
- Authentication lists for users that can access ePHI
- List of individuals and contractors with access to ePHI
- List of software that manages and controls access to the internet
- Physical security means
- ePHI encryption and decryption methods
- Portable media transmission (laptops, cell phones)
- Wireless network access and use
- Procedures for session termination for inactive computer systems
- Policies and procedures for emergency access to electronic information systems
- Policies and procedures for password management
- Secure use of workstations
- Disposal of devices that contain ePHI
This list can be modified depending on the type of covered entity or business associate. The results of the HIPAA audit are compiled in a HIPAA audit report. In the next section, we’ll discuss one of the most important rules within HIPAA — the Security Rule.
HIPAA Security Rule
According to HHS.gov, the official website of the US Department of Health and Human Services, all covered entities and business associates dealing with data protection (PHI) have to follow the HIPAA Security Rule. This rule outlines a series of administrative, technical, and physical safeguards to assure the confidentiality, integrity, and availability of electronic PHI. Let’s overview each of these safeguards.
Administrative safeguards
According to these safeguards, covered entities working with PHI are required to assign a responsible security officer and establish a security management process to make sure that access to all sensitive information is safe and role-based. These safeguards include workforce training and management as well as evaluating compliance with security policies and procedures prescribed by the Security Rule. What does this mean when it comes to custom healthcare software development?
- A risk assessment is a must to make sure your app is HIPAA-compliant. As a rule, it’s a security officer is responsible for predicting potential vulnerabilities and mitigating data breaches they may cause.
- Contingency planning follows defining and assessing risks. It includes deciding on steps to protect PHI and developing an action plan in case of an emergency.
- Role-based access allows you to protect your data from unauthorized access by any third parties.
- Security training is needed to make sure your staff is able to recognize cyberattacks and take required precautions. It includes validating that your contingency plan still works and reporting any incidents.
Physical safeguards
Physical safeguards relate to granting physical access to ePHI stored on-premises, in the cloud, or in a remote data center. They define how to secure workstations and devices from unauthorized access.
- Security of workstations. Ensuring the security of workstations that have access to ePHI includes implementing security systems, video surveillance, and door and window locks as well as securely placing servers and computers.
- Security of personal devices. Anyone who accesses ePHI from their smartphone and other personal devices must follow security policies and recommendations implemented by the organization. For instance, in case of contract termination, an employee must delete any ePHI from their personal mobile devices.
Technical safeguards
This set of safeguards is related to the technologies used to ensure secure access, audit and integrity controls, and transmission security. In terms of healthcare software development, technical safeguards include:
- Implementing access controls. These controls require secure user authentication and safeguarding of emergency access. The latter refers to situations when a hospital management system is damaged or becomes inoperative or an electric power station is out of order. In situations like this, access to ePHI needs to be restored for covered entities. Secure authentication means granting unique access to each medical web app system user. This can be done with a password, smart card, key, or biometric data.
- To ensure audit controls, a developer of health applications needs to implement hardware, software, and procedural mechanisms that examine activities in systems that contain or use protected data. Such an approach presupposes implementing a technical infrastructure and using a risk analysis system to define audit controls that are suitable for your systems.
HIPAA Privacy Rule
The HIPAA Privacy Rule protects the use and disclosure of ePHI. It applies to health plans, healthcare providers that conduct digital healthcare transactions, and healthcare clearinghouses. The Privacy Rule also requires ensuring safeguards to protect the privacy of ePHI. The Office of Civil Rights (OCR) within the Department of Health and Human Services is responsible for enforcing the Privacy Rule regarding compliance activities as well as monetary penalties in case of non-compliance. The rule is constantly updated to remain flexible and comprehensive enough to cover a wide range of instances for use and disclosure of PHI.
The major purpose of the Privacy Rule is to define and limit the circumstances under which patients’ PHI can be used or disclosed. Covered entities are allowed to use or disclose PHI only in two cases:
- If the Privacy Rule either allows or requires the use or disclosure of PHI
- If the individual who is the subject of the information authorizes this use or disclosure in writing
Under the Privacy Rule, there are required disclosures and permitted uses and disclosures. Disclosures must be given:
- to individuals when they request their PHI
- to HHS when conducting a compliance investigation or enforcement action
Permitted uses and disclosures include those:
- to the individual (the data subject)
- for treatment, payment, and healthcare operations
- for which the opportunity is given to agree or object to the use or disclosure (by asking a data subject outright or based on the right to disclose PHI if an individual is incapacitated, in an emergency situation, or unavailable)
- involving incidental use and disclosure (with regard to safeguards under the Privacy Rule and if PHI disclosure is limited to the “minimum necessary”)
- in the public interest and for benefit activities (an individual’s consent isn’t necessary if use or disclosure of PHI falls under 12 national priority purposes)
- concerning a limited dataset (PHI without individual identifiers can be used for research purposes, public health purposes, or healthcare operations)
How to make software HIPAA-compliant
Ensuring compliance with HIPAA requirements for software is a cumbersome process that is achieved by following three basic steps.
Step 1. Conduct a risk assessment
The Department of Health and Human Services explains a risk assessment as defining risks and threats to the confidentiality, availability, and integrity of all PHI that a company produces, obtains, maintains, or shares. Their approach to analyzing risks includes the following components:
- determining where PHI is stored, obtained, maintained, and transmitted
- defining potential risks based on vulnerabilities and creating relevant documentation
- evaluating security practices established to protect PHI and confirming they are used correctly
- assessing potential consequences of a PHI breach
- setting risk vulnerability levels and defining possible impact combinations
- documenting and assessing details to create an action plan if current security processes require improvements

2. Eliminate risks and adjust processes
After performing an initial risk analysis and defining risk factors, the next step is to adjust your existing processes in a way that would help to eliminate the risks.
You can start with training staff on cybersecurity measures, addressing minimum necessary requirements and permitted uses and disclosures of PHI, as well as explaining the use of two-factor authentication.
Once you’re done with the basics, it’s time to proceed to more complex software security tasks like setting internal access controls and acknowledging the consequences of carelessly disclosing PHI.
3. Ensure long-term risk management
Managing potential security risks requires a long-term strategy. As a rule, it starts with implementing a network monitoring tool to deal with some of your risks. Such software is capable of solving complex tasks like:
- using vulnerability scans to detect security threats
- ensuring platform network event monitoring
- analyzing audit trails to check what action affected an operation
- be compliant with the HIPAA Security Rule
- tracking who is logged into the system
- automating event analysis and compliance reporting

There are a number of HIPAA compliance software products you can choose from. You can use several of them at once or implement a unified system to manage all risks in one place. With years of experience in healthcare software development, Yalantis can become your reliable partner in developing a HIPAA compliance system or telehealth platform. Check out our portfolio to learn more.
Compliance mistakes cost more than you think
Cut rework and service costs before they happen with our free ISO 13485 + FDA compliance guide.
Medical devices and FDA regulations
Use of medical devices and the data shared by them is another reason for privacy concerns.
In addition to HIPAA rules healthcare app, developers should follow, there is another set of rules by the Food and Drug Administration (FDA). The FDA is a US federal agency responsible for protecting public health through the regulation and supervision of food safety, medications, and medical devices. Compliance with FDA regulations is as important as following HIPAA rules and is a must for all MedTech and medical device software providers that operate in the US market.
According to the FDA, an mHealth app can be defined as a medical app if it satisfies at least one of the following conditions:
- It’s used as an accessory to a regulated medical device
- It’s used to transform a mobile healthcare software platform into a regulated medical device
This means that FDA guidelines for medical devices will also apply to mobile health applications.
Wrapping up
Complying with HIPAA and other industry laws, regulations, and standards is one of the key elements of custom healthcare software development.
Yalantis has experience developing HIPAA compliance software. If you plan to create a software product that may be subject to HIPAA requirements, we can guide you down the winding road.