As with any complex technology, the Internet of Things (IoT) requires proper realization to serve its purpose. That starts with providing IoT connectivity. Without it, IoT solutions are like a group of orchestral musicians without instruments – full of potential but unable to make separate sounds into a song.
A good example would be a factory filled with machines and sensors to monitor performance. Without connectivity, these sensors become isolated islands of information, unable to alert the system to failures or inefficiencies. Proper connectivity bridges these islands, enabling real-time data flow, decision-making, and automation.
Connectivity in IoT doesn’t just mean “getting online”; it’s about choosing the right kind of connection for each scenario, as this choice impacts performance. Wi-Fi might work well for a smart home but is unsuitable for a remote agricultural field where LoRaWAN or satellite connectivity is better. Similarly, industrial IoT systems often rely on Ethernet for reliability, while consumer wearables leverage Bluetooth for power efficiency.
At Yalantis, we leverage the most suitable connectivity options to ensure flawless performance — from integrating devices with 5G for high-speed, low-latency applications to using LPWAN for long-range, energy-efficient solutions.
The IoT connectivity comparison in this article will help you understand which type of connectivity fits your project and how we can help you build a connected ecosystem that delivers value.
Need help making sense of your IoT setup?
We offer IoT solutions that support your project from the start.
What Is IoT Connectivity?
So, what exactly do we mean when we talk about “IoT connectivity”?
In simple terms, IoT connectivity is the way devices in an Internet of Things system connect to the internet and to each other. It’s what lets a device send and receive data without needing a person to step in, making it one of the most fundamental components of any IoT system.
For example, an IoT device on a delivery truck might use GPS to get location data and include a temperature sensor to track conditions. It sends this information to a central platform so logistics teams can monitor the shipment and react if needed. To do that, the device needs a reliable connection. But without it, the data stays stuck on the device and can’t be used when it’s needed.
Here’s what IoT connections make possible:
- Devices can send and receive data in real time
- Systems can respond automatically to changing conditions
- Businesses can monitor equipment remotely
- Applications can communicate with multiple devices at once
The right connection depends on what the device is doing. Some need to send small amounts of data over long distances. Others need fast responses with high bandwidth. Choosing the right kind of Internet of Things connectivity is a key part of building a system that actually works.
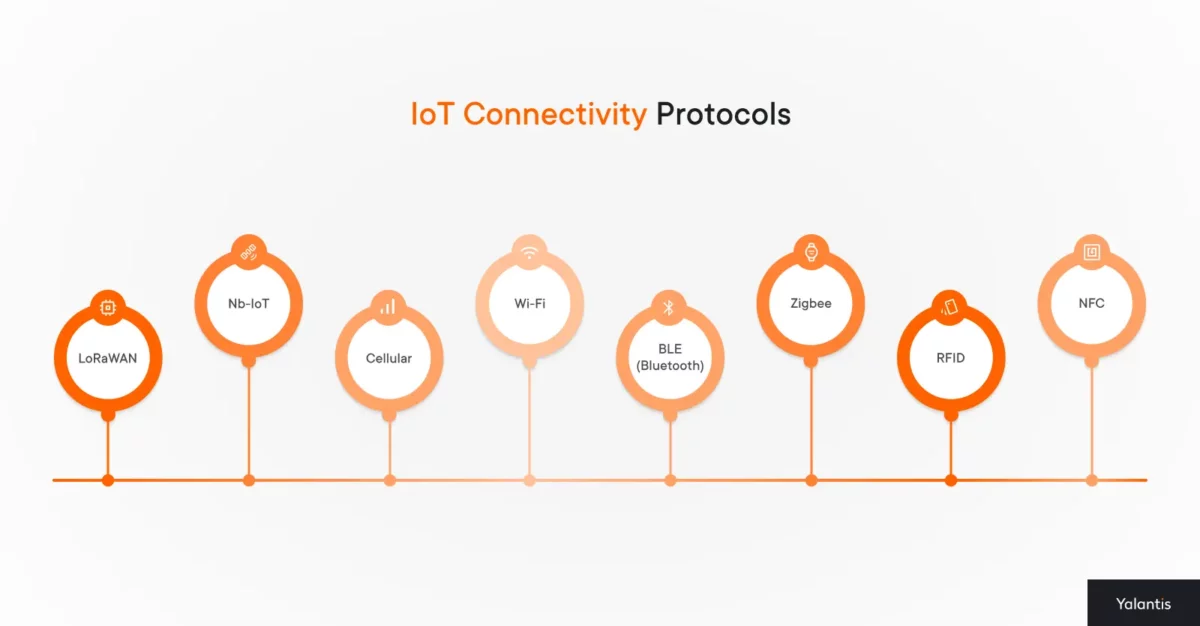
Types of IoT Connectivity Protocols
Now that we’ve looked at the essence of IoT connectivity, let’s look at what those options actually are. IoT connectivity comes in a few main types, each used for different kinds of devices and environments.
Here are the main types:
- Low-Power Wide-Area (LPWA) – Protocols like LoRaWAN and NB-IoT fall into this group. They’re designed for devices that need to send small bits of data over long distances and can’t afford to burn through battery quickly.
- Cellular – This includes LTE, 5G, and similar technologies. They’re a good fit when devices need reliable network access and can handle the extra power use and cost that come with it.
- Short-Range Wireless – Wi-Fi, BLE, and Zigbee are commonly used here. These are best when devices are close together, like inside a home, building, or specific site.
- RFID and NFC – These don’t support constant communication. Instead, they’re used for nearby interactions, such as scanning a badge or reading a tagged item.
8 Best Connectivity Technologies in IoT
To solve the issue of connectivity in IoT, humanity came up with various IoT protocols – the set of standardized rules and formats that enable devices to communicate with each other and with cellular networks. They define how data is transmitted, secured, and processed, ensuring seamless interaction between IoT devices, gateways, and cloud platforms.
Various protocols are designed to meet specific requirements, such as low power consumption, long-range communication, or high-speed data transfer. The choice of protocol depends on the use case – whether it’s smart home devices, industrial automation, or remote monitoring – and may also influence the programming approach used to build the system.
In this section, we’ll explore the most common IoT protocols and their applications, highlighting the pros and cons of each, and how they address diverse connectivity solution requirements.
LoRaWAN
LoRaWAN (Long Range Wide Area Network) is a low-power, long-range protocol designed for IoT devices that need to transmit data in small amounts over vast distances. It operates on unlicensed radio frequencies, making it cost-effective for deployments. LoRaWAN uses a star-of-stars topology, where devices connect to gateways that forward data to central servers. Its focus on energy efficiency allows devices to operate on battery power for years, making it ideal for remote or hard-to-access areas.
LoRaWAN is widely used in applications such as smart agriculture (e.g., soil moisture sensors), utility monitoring (e.g., water meters), and environmental monitoring (e.g., air quality sensors), , connecting remote devices with minimal power consumption. For instance, in agriculture, LoRaWAN-enabled sensors can provide real-time transmit data about field conditions, optimizing water usage and boosting crop yields.
At Yalantis, we integrate LoRaWAN into IoT solutions to create reliable, energy-efficient systems for industries requiring extensive coverage and minimal power consumption. A great example of LoRaWAN field usage is Yalantis’ collaboration with RAKwireless, a Chinese manufacturer of various-purpose IoT devices. This collaboration resulted in the development of several new features for RAKwireless enterprise partners.
Where not to use LoRaWAN connectivity protocol
LoRaWAN might seem like a universal IoT connectivity solution for the majority of IoT solutions, but it’s not. LoRaWAN has relatively slow data rates, high latency, and limited bandwidth. If your business requires high-speed communication and native support for mobility – take a look at some other IoT security protocols. IoT security consulting can help businesses choose the right connectivity solutions based on their security and performance needs. Avoid using LoRaWAN for video streaming, highly interactive apps, or high-speed data transfer.
NB-IoT
Narrowband IoT (NB-IoT) is another cellular-based protocol designed for IoT applications that require reliable connectivity in areas with poor coverage. Operating within licensed spectrum bands, NB-IoT prioritizes low power consumption and wide-area coverage, making it ideal for massive IoT deployments. It supports deep indoor penetration, allowing multiple devices to maintain the right connectivity technology even in basements or urban environments.
NB-IoT is commonly used in smart city projects, such as connected streetlights or waste management systems, and industrial use cases like asset tracking and predictive maintenance. For example, smart parking systems use NB-IoT to monitor available spaces and guide drivers efficiently. At Yalantis, we leverage NB-IoT to develop solutions for clients needing secure, scalable, and power-efficient IoT systems, especially in urban and industrial settings.
The main disadvantage of NB-IoT is its price – the deployment of narrowband systems often requires existing infrastructure upgrades and high maintenance costs. It’s not the best fit for real-time apps and high-frequency sensor data environments.
Cellular
Cellular connectivity solutions, including LTE and 5G, are robust and scalable solutions for IoT applications requiring high-speed, reliable internet access, and wide-area network coverage. While LTE supports most IoT needs today, 5G brings ultra-low latency and higher bandwidth, unlocking possibilities for real-time applications such as autonomous vehicles and remote surgeries. Cellular connectivity often requires SIM-based devices and operates within licensed spectrum bands, ensuring secure and regulated communication. Here’s an appropriate example of cellular connectivity use – our collaboration with an EV charging network from the UK.
Use cases for cellular IoT include fleet management, video surveillance, and mobile point-of-sale systems. For example, connected delivery vehicles use cellular networks to transmit real-time location and performance data to logistics hubs. At Yalantis, we integrate cellular technologies into IoT solutions where speed, reliability, and broad coverage are critical, ensuring seamless connectivity for high-stakes applications.
As for the disadvantages of cellular connectivity, its data plans cost and dependency on network coverage comes to the stage. Cellular IoT connectivity technologies are not the best choice for battery-powered IoT devices and use in the areas with weak coverage.
Wi-Fi
Wi-Fi is a ubiquitous and high-speed wireless IoT connectivity technology option often used in local IoT networks. It provides excellent transmit data throughput and is ideal for environments with reliable power sources, as Wi-Fi is more power-hungry than alternatives like Zigbee or BLE. With advancements such as Wi-Fi 6, the protocol now supports improved device density and reduced latency, making it more IoT-friendly. This approach is similar to what we implemented while collaborating with a large US-based agricultural machinery manufacturer, when we developed a custom solution for energy consumption optimization to improve their operational efficiency and decrease energy consumption.
Wi-Fi is commonly used in smart homes (e.g., security cameras, smart speakers) and enterprise settings (e.g., connected conference rooms). For instance, a smart thermostat in a home can use Wi-Fi to connect to cloud servers, enabling remote control via a smartphone app. At Yalantis, we build IoT solutions that utilize Wi-Fi when high data throughput and simplicity of integration are priorities, particularly for consumer-facing products.
The main weaknesses of Wi-Fi connectivity are its effective range, high energy consumption and security concerns. Do not use Wi-Fi connectivity solutions for deploying on large areas, public outdoor environments or on low-power IoT devices.
Bluetooth Low Energy (BLE)
Bluetooth Low Energy (BLE) is a short-range wireless protocol optimized for low power consumption, making it ideal for portable IoT devices. BLE’s low energy requirements allow devices like wearables and health monitors to run for weeks or months on a single charge. BLE operates within the 2.4 GHz ISM band and supports point-to-point, broadcast, and mesh topologies.
Typical use cases include fitness trackers, smartwatches, and beacon-based systems like indoor navigation. For example, BLE beacons in a shopping mall can guide customers to specific stores while providing promotional information. At Yalantis, we use BLE to develop IoT solutions that prioritize portability, energy efficiency, and seamless user experiences.
Compared to other protocols, Bluetooth has lower range and scalability opportunities, as well as reduced data transfer speed. Also, a lot of Bluetooth devices operating in a small area may cause performance drops for all the devices. We don’t recommend using Bluetooth IoT connectivity solutions for industrial solutions that require long distance or high-speed communication and seamless data transfer.
Zigbee
Zigbee is a low-power, low-data-rate protocol designed for IoT applications that require reliable, mesh-based communication. Its ability to create self-healing cellular networks makes it highly resilient in environments with many IoT devices. Zigbee is often used in smart home and industrial automation systems, where IoT devices need to communicate over short distances but with robust reliability.
Smart lighting systems are a common use case for Zigbee, enabling bulbs, switches, and sensors to communicate without requiring direct Wi-Fi connectivity. At Yalantis, we leverage Zigbee to build IoT solutions that require robust, scalable, and power-efficient network connections, especially in environments with high device density. By the way, we also used this approach in our fitness device integration project, where we built an app that works with multiple wearables. Patients could use the device they’re most comfortable with, and clinics got better-quality health data.
Zigbee’s main disadvantages are even shorter effective range than Wi-Fi, risks of performance issues in high-load areas, and it’s prone to 2.4 GHz environments. It’s not recommended to use Zigbee protocol in the large outdoor areas or on the locations with heavy radio frequency interferences.
RFID
Radio Frequency Identification (RFID) is a short-range technology that uses electromagnetic fields to identify and track objects wirelessly. RFID tags, which can be passive or active, store data that RFID readers can capture. Passive tags draw power from the reader’s signal, while active tags have their own power source for extended range.
RFID is widely used in logistics for inventory management, in retail for anti-theft systems, and in healthcare for patient tracking. For example, RFID tags on warehouse pallets allow businesses to track inventory movements accurately. At Yalantis, we integrate RFID into IoT ecosystems to enhance tracking, automation, and asset management capabilities.
Using RFID protocol is not the best choice for data-heavy apps, or for long real-time monitoring solutions with long-range asset tracking, due to its short read ranges with passive tags and high cost of active tags. Also, RFID is sensitive to environmental factors.
NFC
Near Field Communication (NFC) is a subset of RFID designed for extremely short-range communication (typically within a few centimeters). NFC is primarily used for secure, contactless exchanges of small amounts of data, such as payments or access credentials. Its user-friendly nature and security features make it popular for consumer-facing IoT applications. For better understanding, take a look at how we contributed to improving sustainability for EV charging by helping a European charging network expand beyond cities and serve both tourists and intercity drivers.
NFC is commonly found in smartphones, enabling tap-to-pay systems, ticketing, and secure device pairing. For example, a smartwatch with NFC can allow users to make payments or unlock doors with a simple tap. At Yalantis, we incorporate NFC into IoT solutions to create intuitive, secure, and convenient user experiences, especially for smart wearables and payment systems.
The most obvious disadvantage of NFC protocol is its extremely short range – just a few centimeters due to its physical interaction nature. Also, the NFC protocol has very low data transfer rates, so don’t use it for remote communication apps, automated procedures, or high-throughput data transmission.
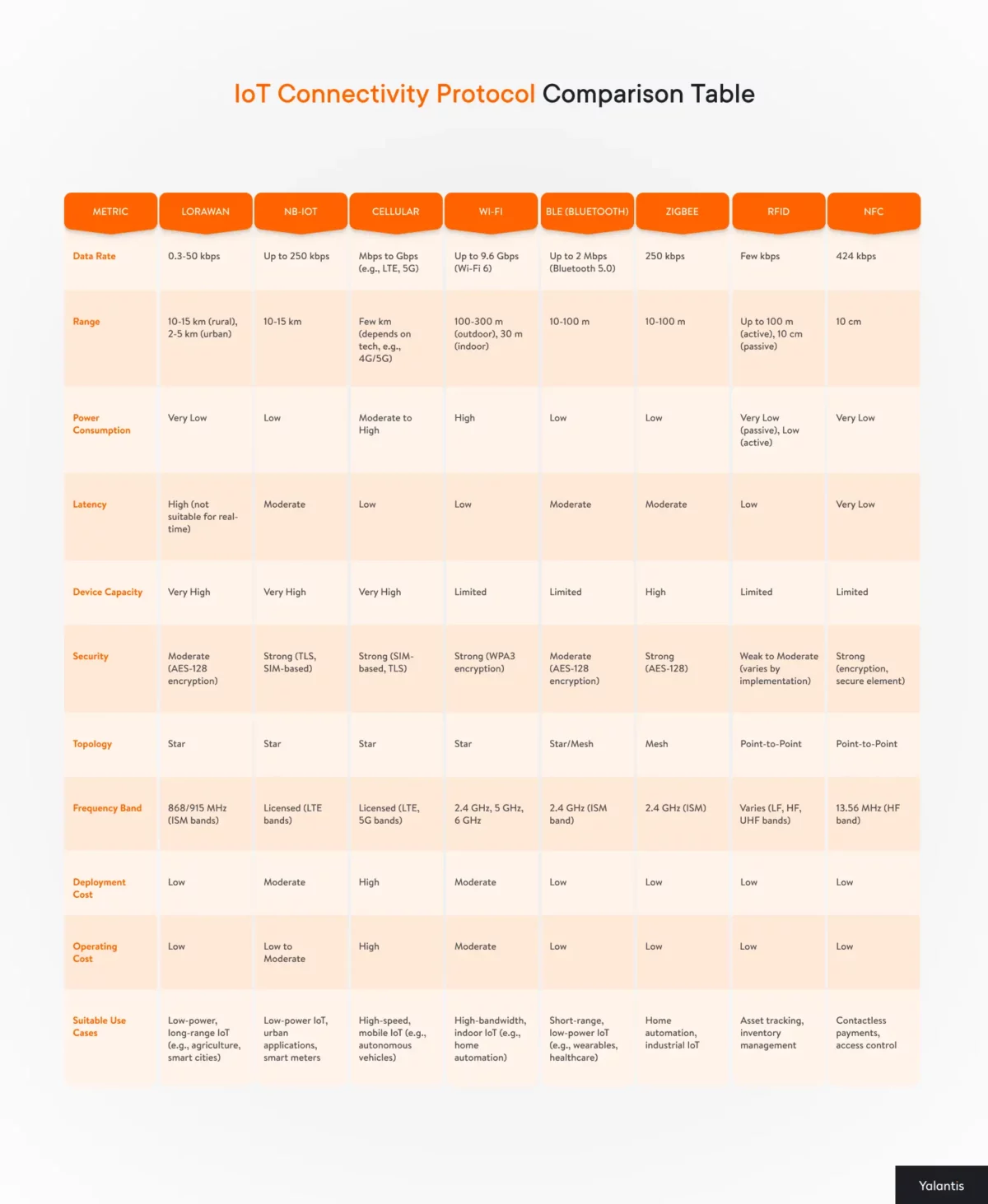
IoT Connectivity Protocols Comparison
If you’re trying to figure out which IoT protocol is right for your project, this table gives a practical overview. It lays out how each option performs when it comes to things like data speed, range, power use, security, and other practical factors.
Some protocols are better for short-range communication in controlled environments. Others are built for long-distance, low-power use in remote areas. This table makes the differences clear and helps you decide which one fits your needs.
How to Choose the Right IoT Connectivity Technology
Here’s a quick checklist to help you match your use case with the right technology, based on what actually matters during deployment:
Coverage (Range)
Need long-range outdoor connectivity in rural or industrial areas? → LoRaWAN or NB-IoT
Urban, wide-area deployments with mobility? → Cellular (LTE/5G)
Local, indoor use in buildings or homes? → Wi-Fi, BLE, or Zigbee
Hyper-local, device-to-device tap interaction? → NFC or RFID
Bandwidth (Data Rate)
High-volume data like video or real-time analytics? → Wi-Fi or Cellular (5G)
Moderate-speed apps like remote diagnostics or firmware updates? → Cellular, NB-IoT
Low-bandwidth telemetry, sensor data, or alerts? → LoRaWAN, Zigbee
Tiny data packets, quick identity verification? → RFID, NFC
Power Consumption
Battery-powered, low-maintenance field devices? → LoRaWAN, NB-IoT, BLE
Devices plugged into constant power or fast-charging systems? → Wi-Fi, Cellular
Energy-critical wearables? → BLE
Passive systems that don’t require internal power? → Passive RFID, NFC
Cost (Deployment + Operations)
Tight budget, wide coverage? → LoRaWAN (unlicensed spectrum, low OpEx)
Telecom-backed reliability but higher cost? → NB-IoT, Cellular
Affordable indoor mesh setups? → Zigbee
Consumer-grade products with Wi-Fi built in? → Wi-Fi, BLE
Low hardware and setup cost for access systems? → RFID, NFC
Security
High-stakes environments (finance, healthcare)? → Cellular, NB-IoT, NFC
Moderate-level needs? → Wi-Fi (WPA3), Zigbee, LoRaWAN
Avoid sensitive data over weakly encrypted RFID unless strictly isolated
Device Density
Large-scale sensor networks (hundreds to thousands of nodes)? → LoRaWAN, NB-IoT, Zigbee
Small clusters of interactive devices? → BLE, Wi-Fi, NFC
Latency Sensitivity
Real-time control or response needed? → Cellular (5G), Wi-Fi, BLE
Tolerant of delays (e.g., periodic sensor readings)? → LoRaWAN, NB-IoT
|
Pro tip: Don’t limit yourself to just one protocol Certain devices rely on long-range coverage. Others need to run for months on battery. And some are built to handle larger data loads. One protocol rarely fits them all without compromise. So why expect one protocol to do it all? A hybrid approach usually delivers better performance and fewer headaches down the line. |
IoT Connectivity-Related Risks
As we discussed previously in the article, a basic element of the IoT solution’s correct performance, IoT connectivity technology enables communication between users, IoT devices, and platforms. This means problematic IoT connectivity brings solid risks, including data leakages and the possibility of downtimes. Connectivity issues also tend to prevent businesses from making timely and accurate decisions.
Let’s dive a little deeper into the IoT connectivity challenges that businesses face when building reliable ecosystems:
Possible Data Leakages
IoT systems handle vast amounts of sensitive data, ranging from personal user information to operational metrics and sensitive business data. Poor connectivity increases the risk of unsecured data, making IoT devices and cellular networks more vulnerable to cyberattacks.
Data leakages may cause:
- Exposing sensitive data during transmission;
- Creating vulnerabilities that hackers can exploit for unauthorized access;
- Breaching data compliance regulations such as GDPR or CCPA.
Which may result in the following risks:
- Legal Repercussions: Data breaches can lead to hefty fines and lawsuits for non-compliance;
- Trust issues: Customers and partners may lose confidence in a company’s ability to protect their information;
- Financial consequences: A single data leakage incident can result in severe financial damage.
Implementing advanced IoT analytics solutions can help analyze, monitor, and secure data transmission, providing greater visibility into potential vulnerabilities and offering preventive solutions.
How to mitigate the data leakages in IoT connectivity-related challenges
Luckily, there are multiple established business practices that will help you reduce the risks of data leakages. First and foremost, using strong encryption protocols to secure data transmissions is a must-have security measure in operating with the Internet of Things.
Also, operating within a secure connection through VPNs or private networks helps to increase the security of your data flow. Updating the device firmware and implementing a secure authentication mechanism like multi-factor authentication helps address the vulnerabilities and prevent unauthorized access to your data.
It’s also never a bad idea to look for the potential weak points in your IoT system. Conducting regular security audits, penetration testing, and vulnerability assessments helps to address potential weaknesses. And don’t forget about following regulations like GDPR or CCPA to avoid legal repercussions.
To prevent human-caused leakages, make sure to conduct personnel training on the best practices in IoT security. And make sure to have a comprehensive incident response plan to minimize the damage in case leakage eventually happens.
Read also: How to Implement an Effective IoT Testing Framework
Risk of Downtimes in Connectivity Technologies
Connectivity issues may lead to device outages and the inability to communicate effectively within the whole Internet of Things ecosystem. This disrupts the flow of information and impacts the reliability of connected systems.
Downtimes cause:
- Interruptions in critical operations, such as supply chain management or production processes;
- Reduced functionality of consumer IoT devices, leading to dissatisfied users;
- Delayed responses to emergencies in sectors like healthcare or industrial automation.
The main risks of downtimes are:
- Operational Losses: Prolonged downtimes directly result in revenue loss and reduced productivity;
- Damage to reputation: Even rare downtimes create negative customer experiences, eroding brand loyalty;
- Overall System Instability: Persistent connectivity issues can cascade into broader system failures.
Investing in reliable cellular networks, redundancy mechanisms, and proactive monitoring can help prevent these downtimes.
Mitigating the risk of downtimes in IoT-related solutions
Building a trustworthy and resilient network infrastructure is your key to avoiding downtimes. This system needs to feature monitoring tools for detecting and addressing issues before escalation, backup connectivity solutions to provide uninterrupted communication in case outages happen, and edge computing for local data processing, which helps to minimize latency and decrease the dependence on centralized systems.
Another great practice to avoid and prevent disruptions is Internet of Things network segmentation. Additionally, the risk of downtimes grows with the data load growth, so make sure to operate with scalable and cloud-based IoT platforms.
And last, but not least – don’t be too confident in your system. Downtime may take place in the most secure system, so make sure to have a detailed downtime response plan in advance, so you can handle the outage fast.
Harder decision making process
IoT thrives on real-time data collection and data processing, which helps to make better business decisions. However poor connectivity delays data transmission, leading to incomplete or outdated information for decision making.
How IoT connectivity harms decision making:
- Decision-making based on inaccurate or outdated data;
- Inability to detect and respond to critical events promptly;
- Lower efficiency in predictive maintenance and other analytics-driven processes.
Affected decision making brings the following risks:
- Missed Opportunities: Delayed insights hinder competitive agility and responsiveness.
- Unnecessarily Higher Costs: Inefficient processes and missed optimizations add expenses, which could be easily avoided;
- Safety Risks: Delayed decisions can lead to accidents or life-threatening situations in industrial or healthcare IoT.
Mitigating the poor decision making in IoT solutions
Operating within reliable and low-latency cellular networks is your key to better decisions. Data transmission delays are much less likely to occur within 5G or private networks. Another proven practice is using edge computing for processing critical data locally, which helps to receive up-to-date information and be less dependent on centralized systems.
It’s hard to imagine making high-quality business decisions without high-quality analytics. Utilize advanced data analytics platforms capable of handling incomplete or delayed data and flagging discrepancies for review. Also, we recommend implementing redundancy systems to ensure continuous data flow, even if partial network failures occur. Internet of Things solutions that incorporate robust analytics and failover mechanisms help businesses improve decision-making and mitigate risks associated with unreliable data.
Read on to learn more about the variety of IoT connection protocols and technologies and to find out which of them fits your IoT project.
Building the Backbone of Your IoT Devices Ecosystem with Yalantis
IoT connectivity is more than just a random technical feature – it’s the foundation that turns isolated devices into intelligent systems capable of transforming both industry and daily life experiences. As we’ve explored, the choice of connectivity protocol directly impacts the success of any IoT solution, influencing factors such as range, power efficiency, data security, and scalability. The correct protocol helps to ensure that IoT devices work seamlessly in their intended environments.
Connectivity is like the nervous system of a body – it ensures that signals are sent, decisions are made, and actions are taken. Without the right IoT connectivity solutions, even the most advanced IoT devices become unresponsive and disconnected, unable to deliver their potential.
A smart city can’t operate its connected streetlights without reliable NB-IoT, just as a wearable health tracker is ineffective without energy-efficient BLE. Choosing the right protocol isn’t just about functionality; it’s about optimizing performance, reducing costs, and future-proofing your IoT solution.
AI consulting companies can assist in selecting and implementing connectivity solutions, or you can hire top IoT experts to ensure your architecture aligns with business goals and supports both scalability and security.
At Yalantis, we understand the complexities of IoT connectivity and specialize in dealing with them. With our backlog of IoT software development projects, we are creating network connectivity solutions that align connectivity protocols with the unique demands of your business. Whether it’s enabling smart agriculture through LoRaWAN, integrating cellular connectivity technologies for high-speed applications, or deploying secure NFC systems for user-friendly payment interfaces, we tailor every IoT project to your needs.
Looking for long-term software support?
We provide full-cycle development for connected products across industries.
FAQ
Which IoT connectivity technologies require SIM cards?
SIM card is required for the performance of cellular-based IoT connectivity technologies, including 5G, LTE, and NB-IoT. SIM card IoTs operate inside licensed spectrum bands. They use SIM cards to provide authentication security, and trustworthy network access, and be able to use global roaming.
Can IoT connectivity protocols be combined within a single ecosystem?
Yes, combining IoT protocols is good for optimizing IoT ecosystems.
Wi-Fi, BLE, and Nb-IoT combination is widely used and effective. Combining devices with various protocols helps profit from their advantages: Wi-Fi for high-speed data, BLE for low-power devices, and NB-IoT for wide-area coverage. This multi-protocol approach ensures efficient, secure, and scalable communication. For example, a smart city may use BLE for indoor tracking, Wi-Fi for local hubs, and NB-IoT for infrastructure monitoring.
How can businesses mitigate IoT connectivity-related downtimes?
Mitigating downtimes involves creating a robust network infrastructure with redundancy mechanisms, backup IoT connectivity options, and proactive monitoring tools to detect and resolve issues early. Edge computing can reduce latency by processing critical data locally. Additionally, segmenting IoT networks and adopting scalable cloud-based platforms ensures uninterrupted operations even under high data loads. A well-defined incident response plan minimizes disruptions during outages.
Which IoT connectivity technology is best for long-distance communication?
If you’re dealing with long-range connectivity for IoT, LoRaWAN is well-suited for remote outdoor areas, and NB-IoT works better in challenging indoor or urban settings where signal penetration is tougher.
What is the most energy-efficient IoT connectivity protocol?
LoRaWAN and BLE are the most energy-efficient protocols for IoT. LoRaWAN works best for remote sensors that send small amounts of data occasionally, while BLE is ideal for short-range, battery-powered modules like wearables or health trackers.
Are IoT connectivity technologies secure?
Yes, but it depends on the protocol. Cellular and NB-IoT offer strong encryption by default, while others like RFID or BLE might require extra security steps depending on how and where they’re used. It’s smart to run a security consultation before deployment to catch weak points early.
Can different IoT connectivity protocols work together?
Yes, IoT systems often combine multiple protocols. Using BLE, Wi-Fi, or NB-IoT across different devices adds flexibility and efficiency, especially when introducing additional functionality across locations. But it takes planning and expertise to get right, or you risk communication gaps and overload.
How does IoT connectivity impact device scalability and cost?
IoT connectivity has a direct impact on both scalability and cost. Some protocols like LoRaWAN are cheaper to scale thanks to lower power use and simpler installation, while cellular options may need more investment but support larger networks. Choosing the right setup early helps avoid costly changes later. If you’re unsure which approach fits your project, feel free to reach out and we’ll talk through the options.