In July 2024, a software update from CrowdStrike caused memory safety errors. Hospitals worldwide were affected. Critical systems failed, putting patients at risk. The same bugs — like use-after-free and buffer overflows — still appear in today’s medical devices.
This is exactly what Rust development services help prevent. It’s a Rust systems programming language built to prevent entire categories of memory and concurrency bugs. It doesn’t use a garbage collector. Instead, it catches problems at compile time before the code runs. That makes it a strong fit for fast, safe software that needs to meet standards like IEC 62304 rust compliance.
Medical device teams face more pressure than ever:
- Regulators expect certified software for medical devices.
- Devices must run on their own, safely, and in real time.
- Old C and C++ code slows teams down and adds risk.
- Systems — from device firmware to cloud — are more complex now.
At Yalantis, we’ve helped clients move from risky, outdated systems to secure, modular ones built in Rust embedded systems in healthcare.
In this article, we’ll show how Rust programming for MedTech helps you:
- Prevent memory safety issues without losing performance.
- Meet IEC 62304 rust compliance standards with confidence.
- Deliver real-time reliability for autonomous medical workflows.
- Build secure architectures for edge-to-cloud medical platforms.
- Plan safe transitions from C/C++ to Rust with minimal disruption.
The stakes are too high to rely on unsafe systems programming. This article provides a clear, actionable path to building software for safety certified medical devices using a proven toolchain.
Is your medical software safety-audit ready?
Learn how to switch from C++ to Rust to ensure memory safety and simplify compliance with medical standards.
Why Legacy Tech Is Holding Back MedTech Firmware
Most medical devices still run firmware written in C or C++. These languages were built decades ago — before today’s security risks or real-time systems existed. They’ve done their job well, but now they slow progress and make it harder to build safe, connected medical devices that can be certified.
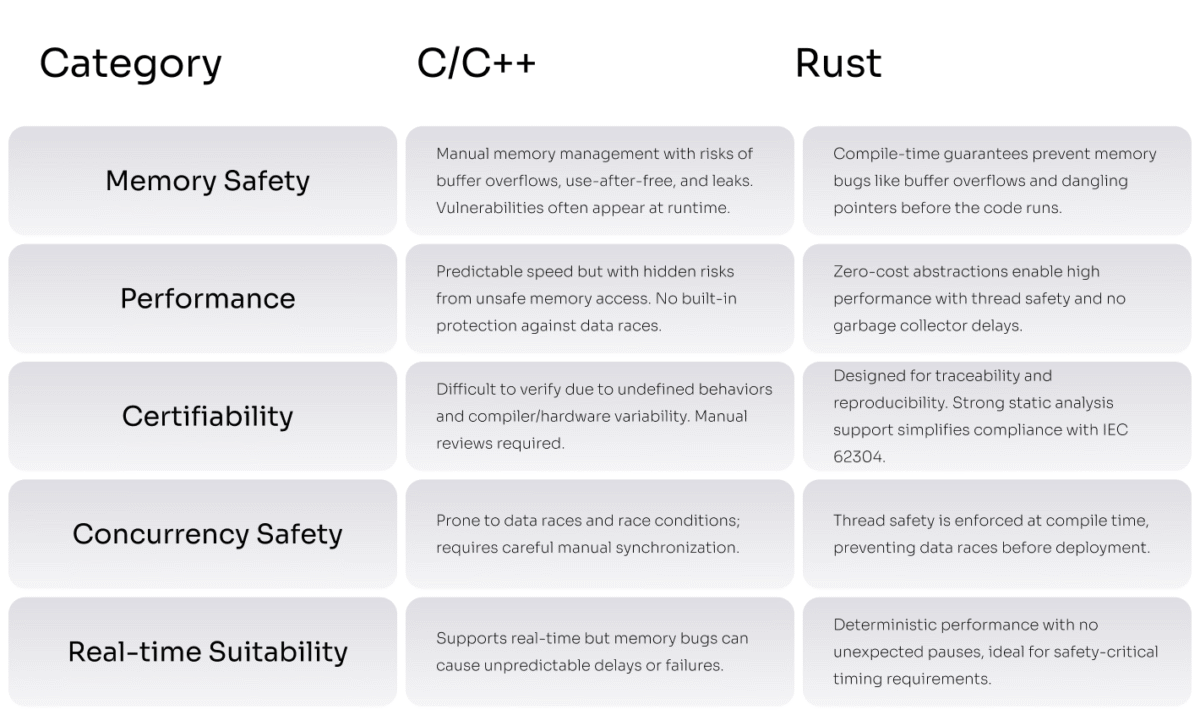
Memory Safety Isn’t Just a Developer’s Problem Anymore
C and C++ give engineers complete control over memory. But that control comes at a cost. Developers have to handle memory themselves — allocating and freeing it. One mistake can lead to serious bugs:
- Buffer overflows that corrupt patient data.
- Use-after-free errors that crash systems during surgery.
- Memory leaks that make long-running devices fail over time.
Heartbleed happened because of a buffer overflow. Microsoft says 70% of its critical security bugs come from memory safety problems. And with medical devices, you can’t fix those flaws later. You have to stop them from happening in the first place.
Certifiability Is Now the Biggest Roadblock
Getting regulatory approval for medical software has always been tough. And with older tech, it’s getting worse. Static analysis tools struggle to verify C or C++ code full of manual memory logic and undefined behavior. Depending on the compiler or hardware, the same code might act differently in the lab than in the field.
That unpredictability makes it hard to meet standards like IEC 62304 rust compliance. Teams end up spending too much time on manual reviews. And with regulators starting to question memory-unsafe code, approvals are taking longer and getting harder.
Legacy Code Can’t Handle Modern Demands
Today’s medical devices do more than collect data. They make decisions. They read sensors in real-time, update themselves over the air, and send secure data to the cloud. Some run many tasks simultaneously — tracking a patient’s vitals, syncing data, and adjusting settings simultaneously. C and C++ weren’t made for this kind of work. Rust was.
What MedTech Needs Now
To meet today’s safety and performance needs, medical systems need a better base — something memory-safe, thread-safe, and fast enough for embedded use. Rust for safety-critical systems gives you all of that.
It blocks memory bugs before the code runs, prevents race conditions, and runs fast without the pause times you get from garbage collectors. It still gives engineers the low-level control they need to write firmware.
With Rust, medical device teams don’t have to choose between speed and safety. You get both.
How Rust Enables Secure and Autonomous Medical Devices
Rust isn’t just about stopping memory bugs. It gives you a solid base for building secure, reliable, and certifiable systems. Here’s how Rust solves the challenging problems that C and C++ can’t.
Memory Safety Without the Performance Hit
Rust uses a unique ownership system and compile-time checks to eliminate memory safety bugs — without slowing things down. When Google added Rust to Android, memory-related bugs dropped by 68%. That same protection is crucial for autonomous medical devices in Rust.
Rust blocks the three significant memory errors:
- Buffer overflows can’t happen. Rust checks array bounds at compile time. C and C++ won’t stop you from reading past the end of an array — but Rust will.
- Use-after-free errors are caught before the code runs. Rust’s ownership rules track memory use and flag invalid access early.
- Memory leaks are avoided. Rust cleans up memory automatically when variables go out of scope — no garbage collector is needed.
It does all this with zero-cost abstractions. That means you write high-level, safe code, but it compiles into fast machine code.
Concurrency Without Risk
Modern medical devices must manage many tasks simultaneously: reading sensors, handling data, and syncing with the cloud. Rust helps you do this safely. Its type system enforces thread safety before you run the code. That means no data races, no weird crashes, and no guesswork.
Rust uses:
- Send and Sync traits to control what data can move between threads.
- Arc and Mutex to safely share and lock data.
- Channels to pass messages without sharing memory.
With these tools, devices can run tasks in parallel — like tracking vitals and sending data — without stepping on their toes.
Fast, Predictable, Embedded Performance
Medical systems need to act fast — and on time. Rust delivers consistent, real-time performance without surprises.
Here’s what makes it ideal for low-level systems programming for medtech:
- No runtime overhead: Rust compiles to native code; no interpreter is needed.
- Tight memory control: You define memory use at compile time, so there are no runtime surprises.
- Direct hardware access: You can talk to sensors and control systems directly.
- Interrupt handling: You can respond in real-time to critical events.
In 2024, the ACM SIGSAC conference highlighted how software for safety-certified medical devices needs this kind of control. Rust fits that need — it’s safe, fast, and works within tight hardware limits.
Ready for Certification
Regulatory approval is still one of the most complex parts of building medical software, but Rust is also gaining ground here.
Here’s why that matters:
- Traceable builds: You can prove how source code turns into machine code — great for audits.
- Repeatable results: Builds are consistent across different systems.
- Built-in static checks: Rust verifies memory safety without needing extra tools.
- Built-in risk reduction: Rust’s safety features map directly to ISO 14971 risk controls.
In short, Rust makes certification easier — and safer — than older languages ever could.
Compliant MedTech engineering
We build software strictly adherent to ISO 13485 and IEC 62304 standards for connected health devices.
Key Use Cases for Rust in MedTech Firmware
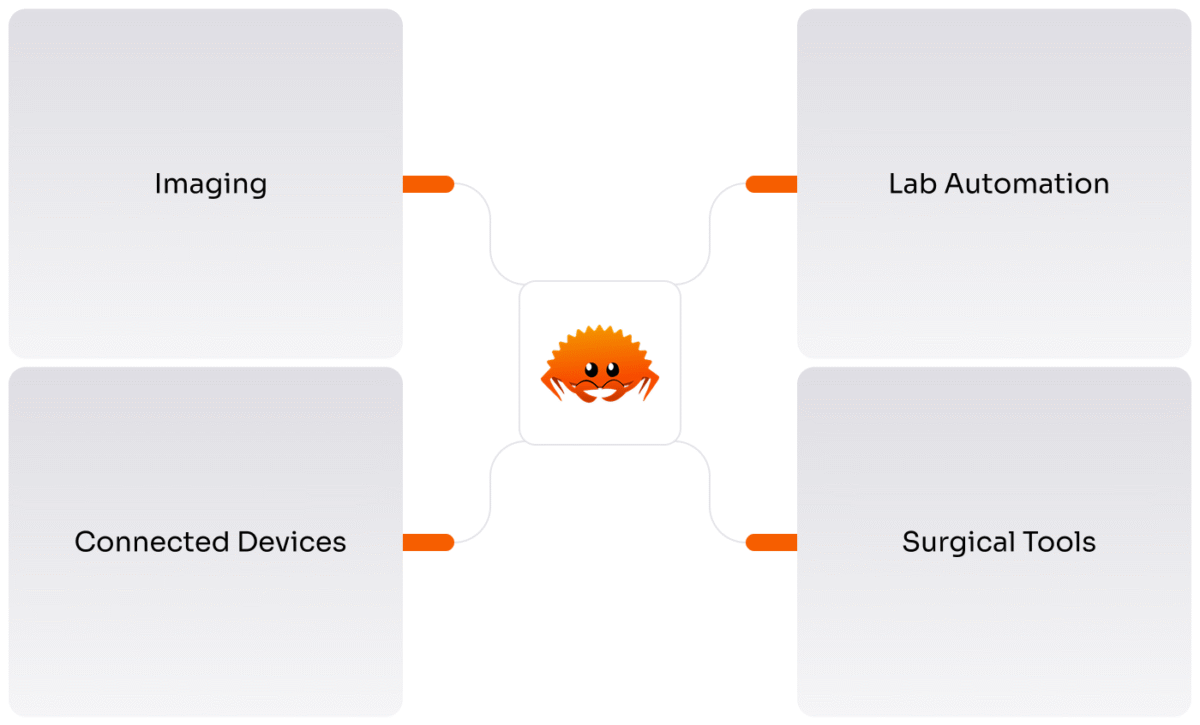
More and more medical device makers are choosing Rust — for good reason. It solves real problems that C and C++ struggle with. Below are four key areas where Rust stands out.
1. Medical Imaging: Handling Big Data, Safely
Medical imaging creates vast amounts of data. A single CT scan can be 500 MB, and a 4D cardiac MRI might top 2 GB. One memory error in this process could distort an image and lead to a wrong diagnosis.
Rust helps prevent that. Its memory safety checks stop buffer overflows that could corrupt pixel data. And its zero-cost abstractions let you write high-level code that runs as fast as C++ without the same risks.
Imagine a heart system that processes live X-rays at 30 frames per second while building 3D models in real-time. In C++, this setup risks memory crashes from race conditions. Rust avoids that by catching errors before the code runs.
Why it works:
- It runs tasks in parallel across multiple CPU cores without memory issues.
- It uses memory predictably, avoiding failures during procedures.
- It supports zero-copy access, speeding up hardware integration.
2. Lab Automation: Precise, Real-Time Control
Lab equipment has to be fast and precise. Devices like robotic arms and pumps must stay in sync down to the microsecond. Languages with garbage collection can’t consistently deliver that level of consistency.
Rust gives you real-time control without surprise slowdowns. Say you’re running a PCR test across 384 wells. You need exact temperature control within 0.1°C — for dozens of cycles. A C++ memory bug could throw off the timing. With Rust, that doesn’t happen.
What Rust gives you:
- Interrupt-driven hardware control without risking memory bugs.
- Real-time performance, free of garbage collection pauses.
- Compile-time safety checks that block sensor read errors before they happen.
3. Connected Devices: Safe, Long-Term Operation
Home health tools — like glucose monitors — send sensitive data and run for years on limited hardware. They must be secure, stable, and updatable, even over flaky networks. Rust blocks buffer overflow attacks, avoids memory leaks, and supports safe APIs for encryption and updates.
Key benefits:
- Safe bootloaders for secure over-the-air (OTA) updates.
- Type-safe cryptography APIs that protect keys and data.
- Memory cleanup is built-in, so you don’t run out of space or connections.
4. Surgical Tools: Concurrency Without Compromise
Robotic surgical tools need extreme accuracy. They process camera feeds, respond to surgeon input, and monitor sensors — all at once.
If those systems share data carelessly, the result can be failure or injury. In C++, managing threads safely is complex and error-prone. Rust makes it safe by default. For example, a robotic surgery system might run motion planning, vision, and safety checks on separate threads. You can do that in Rust without risking data corruption — and without the slowdown of heavy locks.
What Rust makes possible:
- Safe multitasking across control loops with no data races.
- Precise error handling to recover from hardware or sensor faults.
- State validation that blocks dangerous robot behavior before it starts.
By embracing Rust programming for medtech and embedded system development services for healthcare, teams can build the next generation of software for safety-certified medical devices, meeting the demands of certification and real-world use.
Rust and Regulatory Compliance: What’s Changing in 2025
This year marks a major shift in how regulators view software safety. More agencies are pushing to eliminate memory safety bugs from critical devices — the kind of bugs that cause the most serious software failures. At the same time, new certified tools are making Rust for medical devices a real, compliant option for building Rust-embedded systems in healthcare and Rust programming for medtech software.
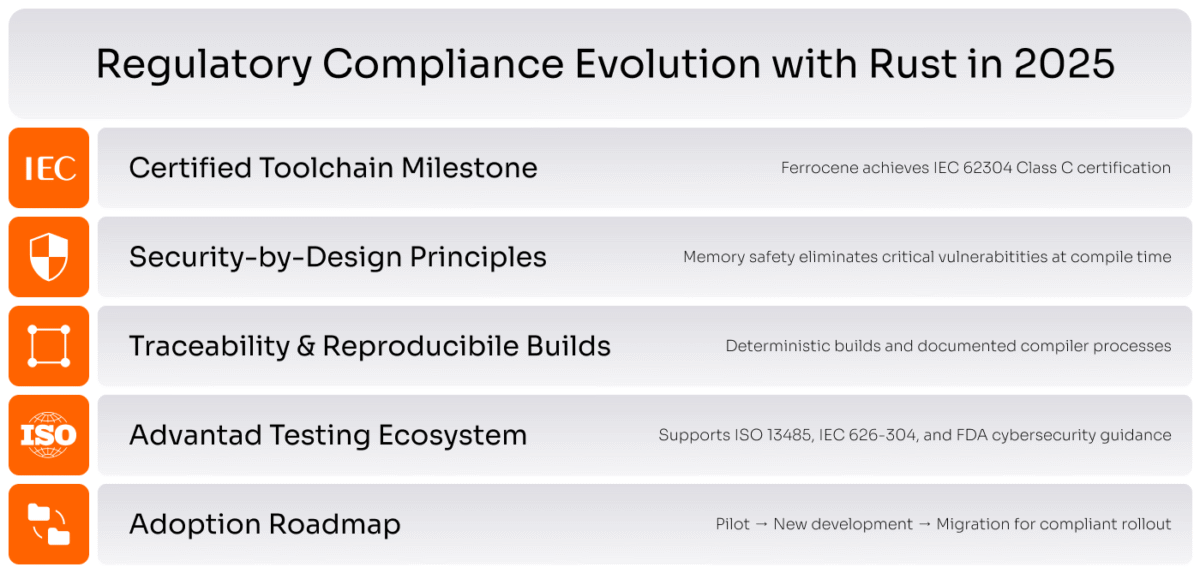
Ferrocene: The First Certified Rust Toolchain
In late 2024, Rust cleared a significant hurdle. The Ferrocene compiler became the first Rust toolchain to get IEC 62304 rust compliance Class C certification — the highest level for software for safety-certified medical devices. With full regulatory backing, you can now build life-critical systems like ventilators and surgical robots in Rust.
Ferrocene includes all the documentation and traceability that regulators want:
- Proof that Rust code turns into machine code in a safe, trackable way.
- Builds that consistently produce the same binary, no matter where you compile.
- Built-in memory safety checks that reduce the need for time-consuming manual reviews.
Rust Matches Today’s Regulatory Goals
The FDA and other agencies now expect “secure by design” software. They want developers to prevent bugs up front — not patch them later.
Rust supports that approach. It blocks 70% of the bugs that lead to serious vulnerabilities in C/C++ systems. And it helps with:
- Safer coding practices baked into the language.
- Fewer security patches after release.
- Automatic Software Bill of Materials (SBOM) tracking using Cargo, Rust’s built-in package manager.
Rust makes meeting IEC 62304 rust compliance easier because it catches safety issues during development — not during expensive reviews.
Mature Tools for Testing and Verification
Medical software needs proof that it works and won’t fail. Rust now has the tools to support that kind of deep testing:
- Property-based tests (like QuickCheck) generate thousands of edge cases automatically.
- Formal verification (with tools like Kani) proves code behavior mathematically.
- Hardware-in-the-loop testing lets you simulate real-time responses without actual devices.
- Code coverage tools make audits easier during regulatory reviews.
Rust’s borrower checker also helps. It prevents memory problems while you code — something C/C++ static analysis tools can’t always do.
Global Standards Are Moving Toward Rust
Regulators and standards groups are shifting focus to languages that prevent memory bugs entirely:
- ISO 13485 pushes for risk-based development — which Rust naturally supports.
- IEC 62304 rust compliance rewards software that avoids whole classes of errors.
- FDA cybersecurity guidance (2023) asks for proof of secure development, not just tests.
The trend is clear: testing isn’t enough anymore. You need to build safety from the start. Rust does that. This makes rust systems programming for medical devices an essential approach going forward.
How to Adopt Rust, Step by Step
If you’re in medical device development, here’s how your team can start using Rust:
- Right now (2025): Try Rust with Ferrocene on non-critical systems. Use these pilots to learn and refine workflows.
- Next phase (2025–2026): Use Rust for new product development — especially when filing new submissions.
- Long-term (2026+): When updating existing products, use change controls to replace old, unsafe code with Rust gradually.
The sooner you begin, the easier it will be to stay compliant — especially in areas requiring Rust for autonomous medical devices and low-level systems programming for medtech.
When Rust Is the Right Choice for Your Medical Device Project
Adopting Rust isn’t about following hype — it’s a deliberate move to improve safety, reduce technical debt, and streamline compliance. While Rust won’t be necessary for every MedTech project, specific scenarios make it the clear long-term winner.
Starting from Scratch: Build for Safety and Security from Day One
New product development in 2025 offers a rare opportunity to avoid the complexity and risk of legacy languages like C/C++. Starting with Rust means building in safety, maintainability, and security from the start.
Rust is the ideal fit for:
- AI-driven autonomous systems
Devices that make real-time treatment decisions — like closed-loop insulin pumps — need strong memory guarantees. Rust eliminates critical bugs at compile time without sacrificing performance. - Connected medical devices
Devices integrated with cloud or mobile apps benefit from Rust’s secure networking libraries and strong typing, which help prevent protocol errors and insecure update channels. - Multithreaded embedded systems
Modern medical devices often run multiple tasks in parallel. Rust prevents data races by design, catching dangerous concurrency bugs before the code runs.
Rewriting Legacy Firmware: Replace Risk with Robust Infrastructure
Maintaining aging C/C++ firmware under rising regulatory pressure is increasingly unsustainable. In many cases, rewriting in Rust is not only safer — it’s more cost-effective.
Consider rewriting when:
- Memory bugs are recurring
Frequent issues like buffer overflows or use-after-free errors suggest structural problems. Rust makes these errors impossible by enforcing safe memory handling at compile time. - Compliance gaps limit progress.
Old code often lacks the traceability needed for IEC 62304. Certified Rust toolchains like Ferrocene produce the qualification artifacts needed for regulatory audits. - Performance is being sacrificed for safety.
Defensive C++ code often adds runtime checks to avoid crashes. Rust shifts safety checks to compile time, improving performance without compromising integrity. - Maintenance costs are rising.
As legacy systems grow, C++ becomes harder to evolve. Rust’s strong type system, modular design, and safety guarantee reduced bugs and increased development speed.
Rust for Embedded Systems: Control Without Compromise
Medical firmware demands a precise balance: low-level hardware control, real-time responsiveness, and strict safety requirements. Rust delivers on all three fronts.
Rust is especially strong when:
- Deterministic performance is essential
Devices like surgical robots or ventilators can’t tolerate unpredictable delays. Rust provides predictable, pause-free execution without garbage collection. - Custom hardware interfaces are involved.
Rust gives engineers direct register access and hardware abstractions like C but with built-in correctness and safety. - You need performance without tradeoffs.
IEC 62304 Class C systems traditionally required a compromise between speed and verifiability. Rust removes that tradeoff with compile-time safety and C-like performance. - You rely on multiple vendors and APIs
Rust’s type system and modular design reduce the risk of bugs when integrating third-party code or hardware drivers.
Success Requires Cross-Functional Collaboration
Adopting Rust impacts more than code — it touches tooling, compliance processes, and engineering culture. Successful rollouts come from cross-disciplinary collaboration:
- Rust engineers bring expertise in safety, concurrency, embedded design, and modern system architecture.
- MedTech domain experts contribute knowledge of regulatory frameworks, clinical risk, and product classification.
Together, these teams can:
- Build device architectures that are both safe and scalable.
- Align with IEC 62304, ISO 13485, and FDA cybersecurity expectations.
- Create phased migration plans for legacy systems.
- Train internal teams in memory-safe development practices.
The Bottom Line: A Platform for Sustainable Innovation
Rust is more than a language — it’s a strategic foundation for building safe, future-ready medical systems.

Yalantis: Rust Firmware Engineering for Medical Devices
Developing firmware for medical devices demands a deep understanding of hardware intricacies, stringent regulatory standards, and the critical consequences of software failure. At Yalantis, we build embedded systems in Rust with the rigor, traceability, and maintainability that highly regulated environments require.
Practical Rust Applications Across MedTech
We’ve leveraged Rust to modernize and build software in multiple medical device domains:
- Diagnostics
Real-time firmware for lab automation and patient monitoring platforms where timing precision and data integrity are non-negotiable. - Connected Care
Embedded software powering home health devices and remote monitoring solutions, including encrypted communications and secure over-the-air (OTA) updates. - Medical Robotics
Deterministic control firmware for surgical tools and automation systems — engineered for safe concurrency and precise hardware control, eliminating memory safety risks.
In every case, Rust helps us eliminate entire classes of bugs that typically demand defensive coding and ongoing patches in C or C++.
Engineering and Regulatory Expertise Under One Roof
“Using Rust in medical firmware isn’t about chasing trends. It’s about writing software that doesn’t fail in ways we’ve seen fail for years.”
— Den Rudenko, CEO, Yalantis
Our team blends deep Rust expertise with in-depth knowledge of medical standards. We build systems compliant with IEC 62304 and ISO 14971 from day one, designing for memory safety, real-time responsiveness, and traceability throughout the development lifecycle.
We help clients to:
- Architect solutions aligned with regulatory controls from the outset.
- Optimize firmware for resource-constrained, time-sensitive hardware.
- Transition off legacy codebases smoothly without disrupting timelines.
End-to-End Partnership: From Architecture to Long-Term Support
Our collaboration goes beyond writing code. We partner with you across the full product lifecycle — from hardware evaluation and risk assessment to maintaining deployed systems securely for years.
|
Planning & Design – Analyze existing systems and define Rust integration points. |
Development – Use certified Rust toolchains to ensure standards compliance. |
Support & Maintenance – Maintain thorough documentation for audits and regulatory needs. |
Structured Rust Adoption Without Disruption
Introducing Rust requires careful planning to fit within existing medical device development workflows. We work alongside your teams to enable adoption without compromising release schedules or regulatory strategies.
Our support includes:
- Training engineers transitioning from C/C++ to Rust.
- Integrating Rust development within your Quality Management System (QMS).
- Mapping Rust’s safety guarantees to regulatory requirements.
- Planning projects aligned with your product roadmap — not just the latest technology trends.
Built to Last: Long-Term Reliability and Maintainability
Medical firmware must remain reliable, maintainable, and secure for many years post-deployment. We don’t just deliver the first release — we stay involved for the long haul.
Our ongoing support covers:
- Security updates driven by real threat intelligence, not marketing checklists.
- Performance tuning as hardware and operational constraints evolve.
- Knowledge transfer to ensure your teams remain independent and empowered.
At Yalantis, we approach Rust development the way medical device teams approach design: methodically, transparently, and with clear accountability. Rust brings powerful new safety guarantees to embedded systems. We bring the experience to apply those guarantees in the real world — with no added risk or noise.
Conclusion: Rust Is Ready for MedTech
Rust has evolved from a promising language to a stable, supported, and production-proven solution — especially for embedded systems where memory safety, real-time guarantees, and regulatory clarity are paramount. Rust offers what legacy toolchains cannot for medical device firmware: the ability to write low-level, high-performance code without risking undefined behavior.
From simple microcontroller sensors to complex surgical platforms, Rust delivers on the essential demands of modern MedTech:
- Eliminates standard failure modes caused by memory misuse.
- Enables precise, real-time control while maintaining rigorous safety guarantees.
- Integrates seamlessly with certified Rust toolchains like Ferrocene for regulatory compliance.
At Yalantis, we help medical device teams adopt Rust with confidence. Whether you’re rewriting legacy C++ firmware hitting its limits or building new products on a safer foundation, we provide the architecture, implementation expertise, and regulatory insight to make Rust viable and compliant from day one.
Plan your medical device roadmap
Discuss how Rust can make your device safer and your certification process smoother.
FAQ
Why choose Rust over C or C++ for safety-critical medical firmware?
Rust eliminates entire categories of memory errors — like buffer overflows and data races — at compile time. This reduces defect rates and shortens debugging cycles in safety-critical systems. Unlike C/C++, Rust provides low-level control without relying on runtime workarounds or manual memory management.
Can Rust-based firmware meet IEC 62304 and FDA cybersecurity requirements?
Yes. With certified toolchains like Ferrocene, Rust supports IEC 62304 Class C development and the traceability and static analysis requirements found in FDA and EU MDR guidance. Yalantis designs architectures and documentation to fit your existing quality management and regulatory workflows.
What types of medical devices benefit most from using Rust?
Rust is especially well-suited to embedded systems where reliability, real-time performance, and long-term maintainability are critical. This includes connected diagnostic tools, surgical robotics, infusion pumps, ventilator control systems, and wearable sensors.
Can Yalantis help migrate existing C/C++ firmware to Rust without delaying certification?
Yes. We’ve developed migration strategies that align with your release schedule and certification timelines. Our approach avoids wholesale rewrites, focusing instead on targeted Rust integration in high-risk or high-maintenance components — like communication protocols, sensor data handling, or critical control loops.
Do you offer architecture consulting and development support for Rust-based medical devices?
We do. Yalantis provides end-to-end services: system architecture design, hardware abstraction layer development, secure communications, regulatory documentation, and post-deployment support. We also work with your in-house teams to build sustainable Rust expertise through training and process integration.








